Question: Several basic principles or reasons make psychological social engineering effective. These includes authority, intimation, consensus, scarcity, urgency, familiarity, and Truest. Following table Principle Description Example
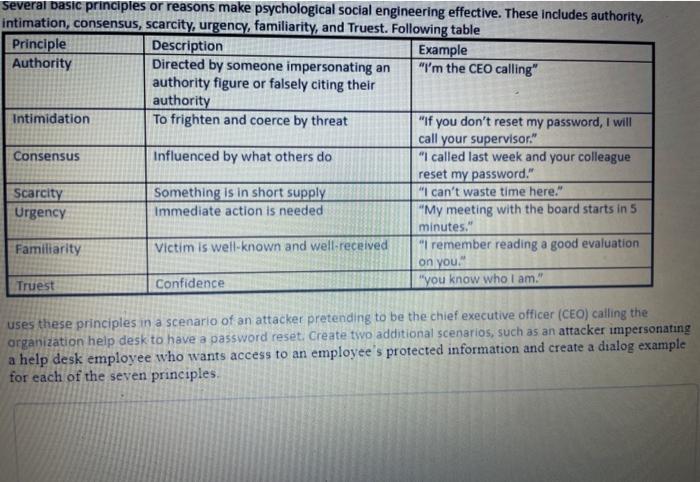
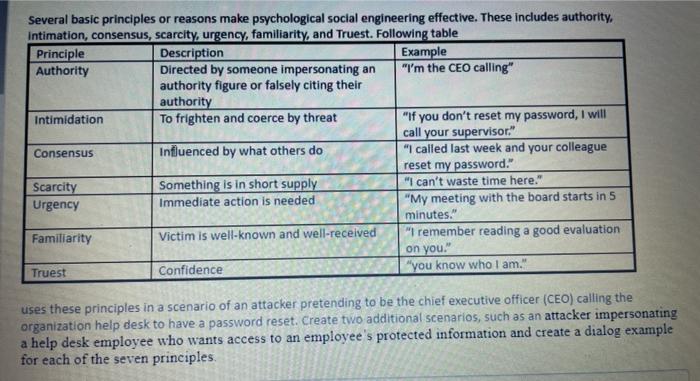
Several basic principles or reasons make psychological social engineering effective. These includes authority, intimation, consensus, scarcity, urgency, familiarity, and Truest. Following table Principle Description Example Authority Directed by someone impersonating an "I'm the CEO calling" authority figure or falsely citing their authority Intimidation To frighten and coerce by threat "If you don't reset my password, I will call your supervisor." Consensus Influenced by what others do "I called last week and your colleague reset my password." Scarcity Something is in short supply "I can't waste time here." Urgency Immediate action is needed "My meeting with the board starts in 5 minutes." Familiarity Victim is well-known and well-received "I remember reading a good evaluation on you Truest Confidence "you know who I am." uses these principles in a scenario of an attacker pretending to be the chief executive officer (CEO) calling the organization help desk to have a password reset Create two additional scenarios, such as an attacker impersonating a help desk employee who wants access to an employee's protected information and create a dialog example for each of the seven principles Several basic principles or reasons make psychological social engineering effective. These includes authority, Intimation, consensus, scarcity, urgency, familiarity, and Truest. Following table Principle Description Example Authority Directed by someone impersonating an "I'm the CEO calling" authority figure or falsely citing their authority Intimidation To frighten and coerce by threat "If you don't reset my password, I will call your supervisor." Consensus Influenced by what others do "I called last week and your colleague reset my password." Scarcity Something is in short supply "I can't waste time here." Urgency Immediate action is needed "My meeting with the board starts in 5 minutes." Familiarity Victim is well-known and well-received I remember reading a good evaluation on you." Truest Confidence "you know who I am." uses these principles in a scenario of an attacker pretending to be the chief executive officer (CEO) calling the organization help desk to have a password reset. Create two additional scenarios, such as an attacker impersonating a help desk employee who wants access to an employee's protected information and create a dialog example for each of the seven principles a
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


