Question: Software security Assessment 1. When a shell variable containing a shell function definition is passed down to a child process as an environment variable, what
 Software security Assessment
Software security Assessment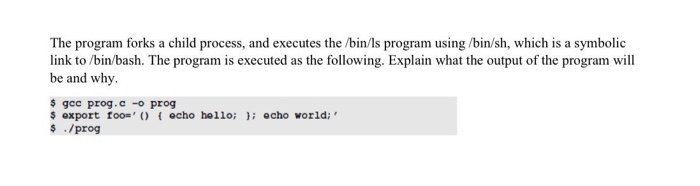
1. When a shell variable containing a shell function definition is passed down to a child process as an environment variable, what is going to happen to the function definition? 2. Instead of putting an extra shell command after a function definition, we put it at the beginning (see the following example). We then run Bash, which is vulnerable to the Shellshock attack. Will the shell command echo world be executed? $ export foo='echo world; 0 { echo hello;}' $ bash 3. For the Shellshock vulnerability to be exploitable, two conditions need to be satisfied. What are these two conditions? 4. Instead of using a function definition in the Shellshock attack against CGI programs, can we directly put shell commands inside the User-Agent field, so when Bash is triggered, the shell command can be executed? 5. We run "nc -Ivp 7070" on Machine 1 (IP address is 10.0.2.6), and we then type the following command on Machine 2. Describe what is going to happen? $/bin/cat /tep/10.0.2.6/7070 >&0 6. Consider the following program #include
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


