Question: Text: Use the following code fragment: Loop: LD R2,0(R1) ;load R2 from address 0+R1 DADDI R3,R2,#2 ;R3=R2+2 DADD R2,R2,R3 ;R2=R2+R3 SD 0(R1),R2 ;store R2 at
Text:
Use the following code fragment:
Loop: LD R2,0(R1) ;load R2 from address 0+R1 DADDI R3,R2,#2 ;R3=R2+2 DADD R2,R2,R3 ;R2=R2+R3 SD 0(R1),R2 ;store R2 at address 0+R1 DSUB R4,R1,R3 ;R4=R1-R3 BNEZ R4,Loop ;branch to Loop if R4=!0
Use the classic RISC five-stage integer pipeline and assume all memory accesses take 1 clock cycle.
Show the timing of this instruction sequence for the basic 5-stage RISC pipeline with full forwarding or bypassing hardware. Assume that a conditional branch is evaluated at the decode stage, and the fetch of the target instruction is delayed until the branch direction is known. Use 'F', 'D', 'X', 'M', 'W' for stages, '-' for a stall, '=' for indicating delayed fetching due to waiting for branch resolution, and 'b' for all blanks.
Image:
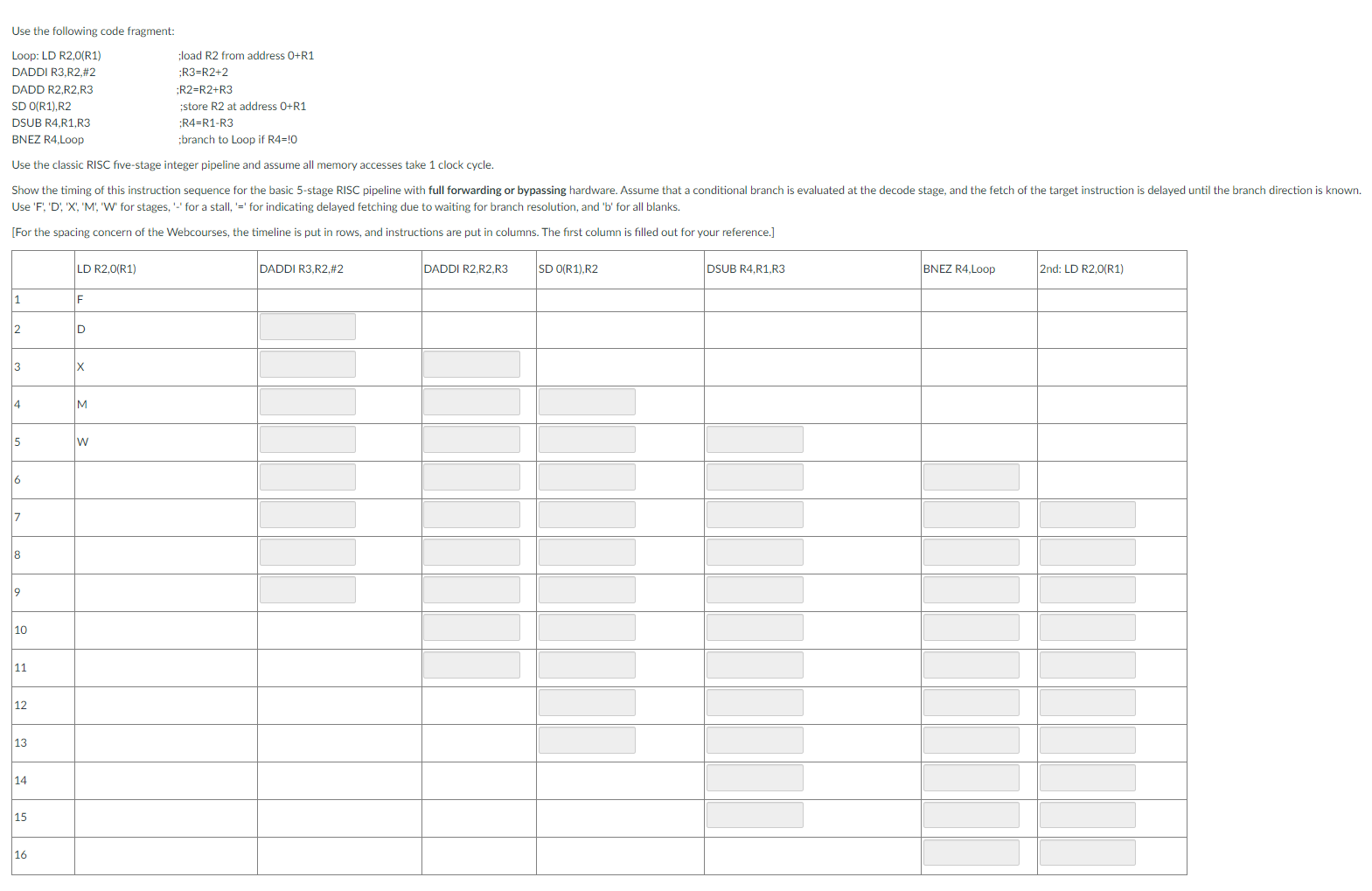
Use the following code fragment: Use the classic RISC five-stage integer pipeline and assume all memory accesses take 1 clock cycle. Use 'F', 'D', 'X', 'M', 'W' for stages, '-' for a stall, '=' for indicating delayed fetching due to waiting for branch resolution, and 'b' for all blanks. [For the spacing concern of the Webcourses, the timeline is put in rows, and instructions are put in columns. The first column is filled out for your reference.]
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


