Question: The base group in CVSS defines exploitablity metrics that indude certain vectors. Which of these is Nor one of those vectors? Atiack vectoe Atack complesily
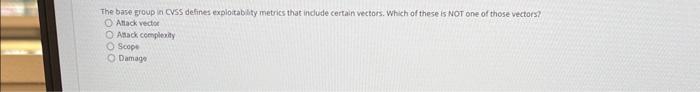
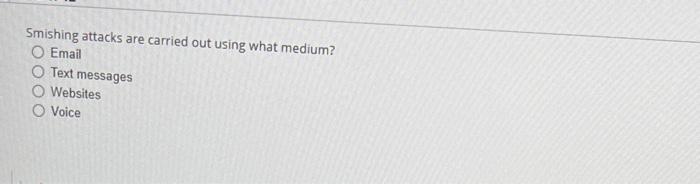
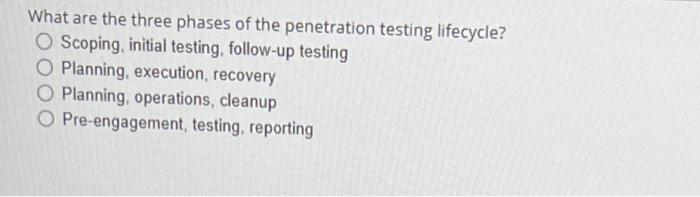
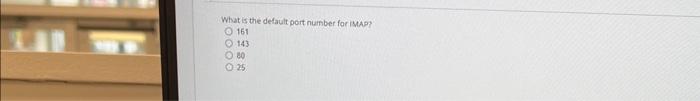
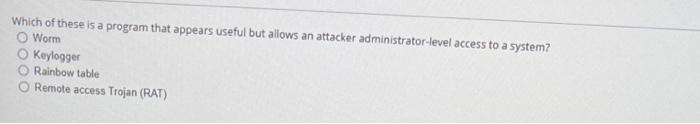

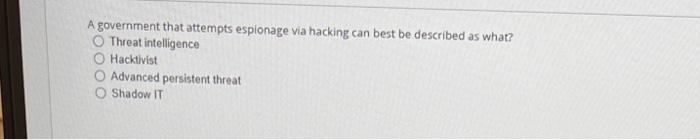


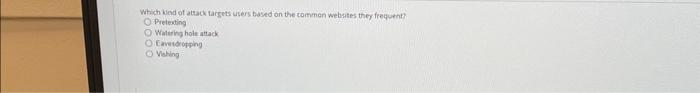
The base group in CVSS defines exploitablity metrics that indude certain vectors. Which of these is Nor one of those vectors? Atiack vectoe Atack complesily Scope Damage Smishing attacks are carried out using what medium? Email Text messages Websites Voice What are the three phases of the penetration testing lifecycle? Scoping, initial testing, follow-up testing Planning, execution, recovery Planning, operations, cleanup Pre-engagement, testing, reporting What is the default port number for ivAP? 161 143 co. 25 Which of these is a program that appears useful but allows an attacker administrator-level access to a system? Worm Keylogger Rainbow table Remote access Trojan (RAT) What is the goal of a bluesnarfing attack? Data theft Unauthorized network access Denial of service Holding data for ransom with encryption A government that attempts espionage via hacking can best be described as what? Threat inteligence Hacktivist Advanced persistent threat Shadow IT E Drernar Which kied ot athack targets users based on the cotrenen websites they frequent? Pretexting Watering hols attack favesdeotiping Vieting
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


