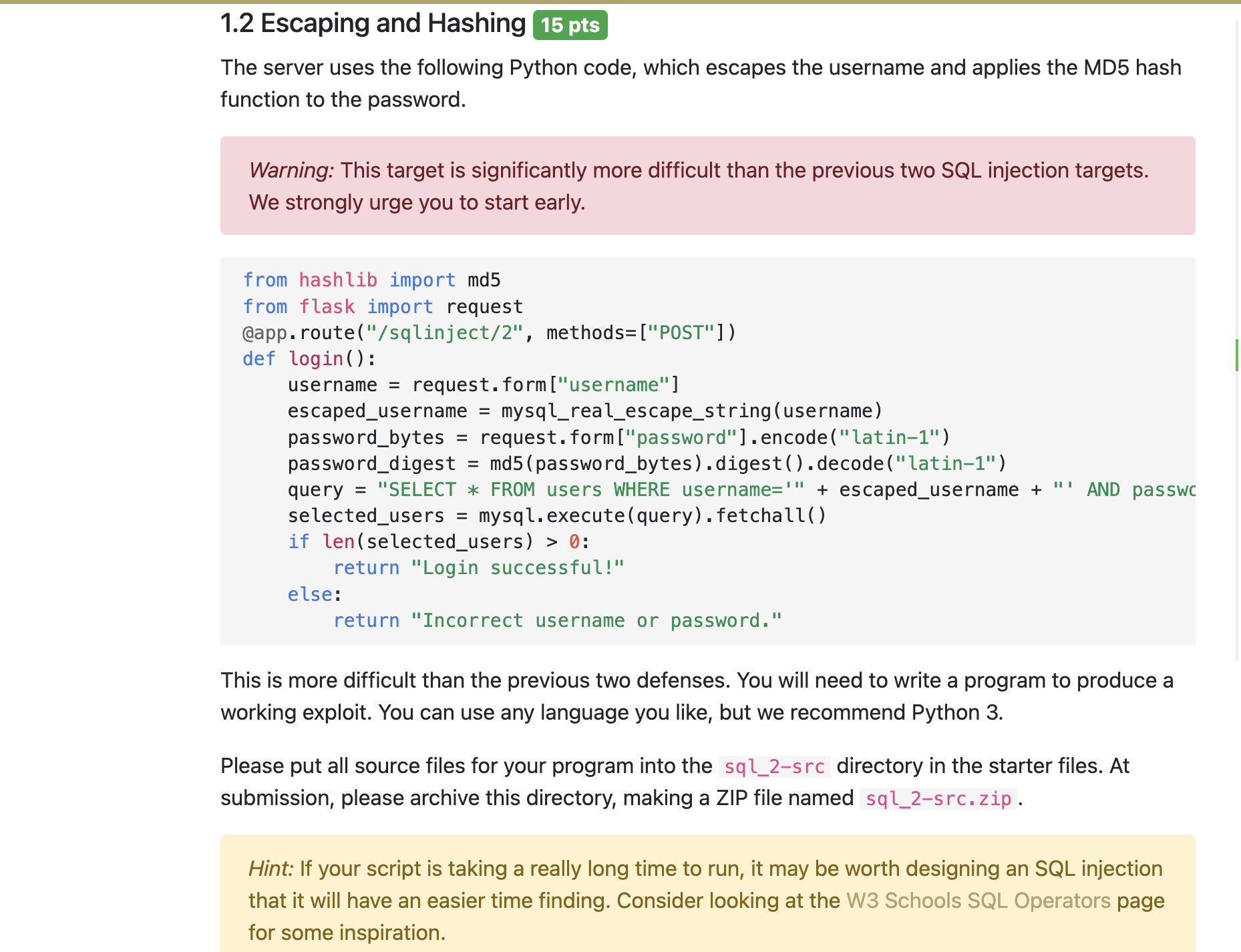
Question: The server uses the following Python code, which escapes the username and applies the MD 5 hash function to the password. Warning: This target is
The server uses the following Python code, which escapes the username and applies the MD hash function to the password.
Warning: This target is significantly more difficult than the previous two SQL injection targets. We strongly urge you to start early.
from hashlib import md
from flask import request
@app.routesqlinject methodsPOST
def login:
username request.formusername
escapedusername mysqlrealescapestringusername
passwordbytes request.formpasswordencodelatin
passworddigest mdpasswordbytesdigestdecodelatin
query "SELECT FROM users WHERE username escapedusername AND passwc
selectedusers mysqlexecutequeryfetchall
if lenselectedusers:
return "Login successful!"
else:
return "Incorrect username or password."
This is more difficult than the previous two defenses. You will need to write a program to produce a working exploit. You can use any language you like, but we recommend Python
Please put all source files for your program into the sqlsrc directory in the starter files. At submission, please archive this directory, making a ZIP file named sqlsrczip.
Hint: If your script is taking a really long time to run, it may be worth designing an SQL injection that it will have an easier time finding. Consider looking at the W Schools SQL Operators page for some inspiration.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


