Question: This problem concerns the following code, for which you are to design a buffer overflow attack such that when it is run the program will
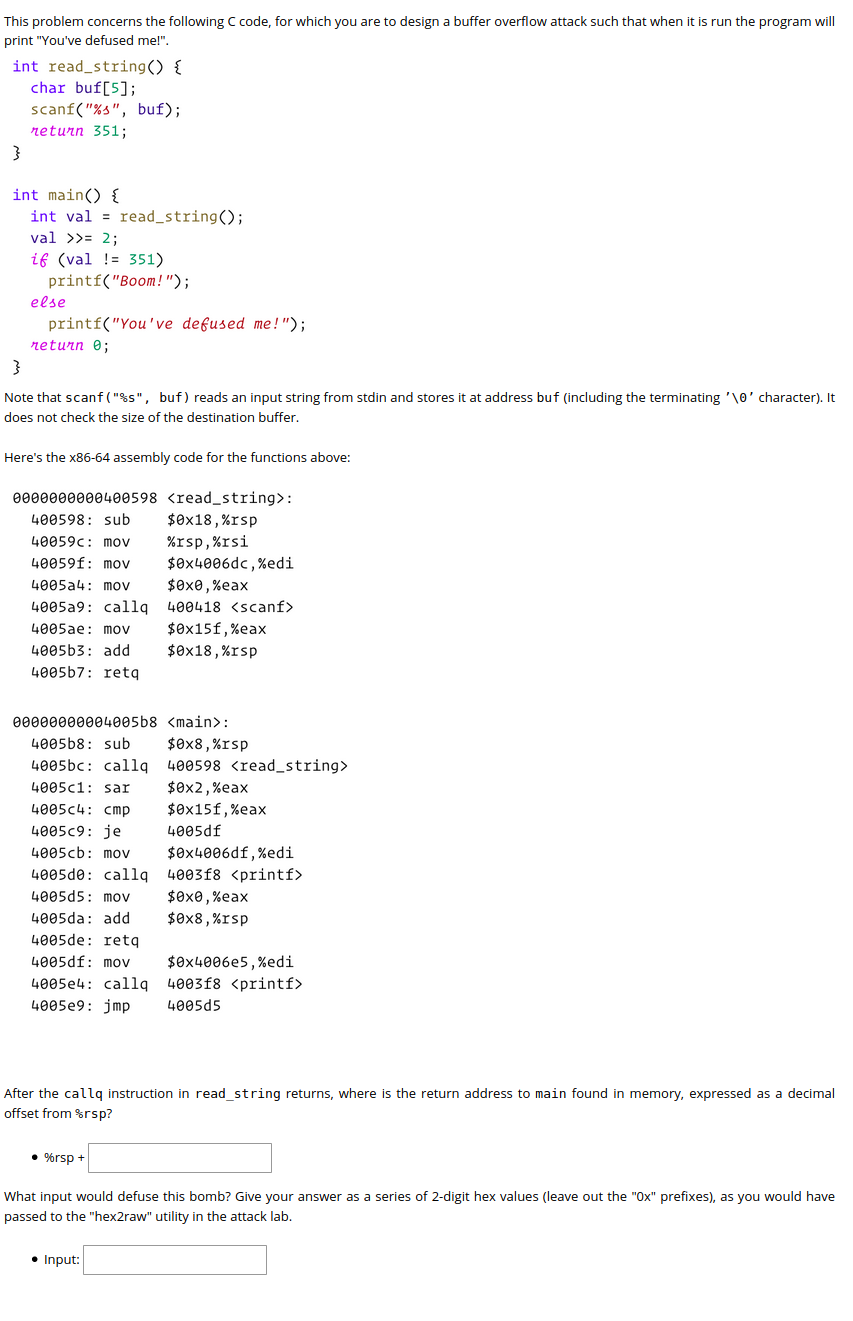
This problem concerns the following code, for which you are to design a buffer overflow attack such that when it is run the program will print "You've defused me!". int read_string() { char buf[5]; scanf("%s", buf); neturn 351; } int main() { int val = read_string(); val >>= 2; if (val != 351) printf("Boom!"); else printf("You've defused me!"); return; } Note that scanf("%s", buf) reads an input string from stdin and stores it at address buf (including the terminating '\0' character). It does not check the size of the destination buffer. Here's the x86-64 assembly code for the functions above: 0000000000400598
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


