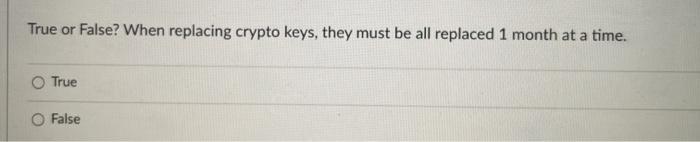
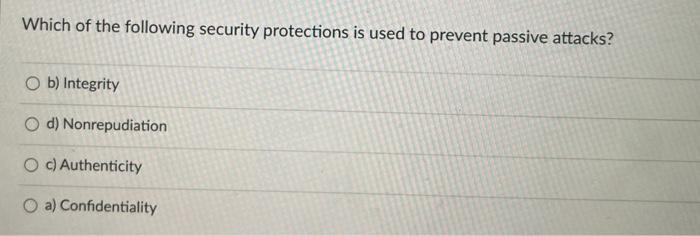
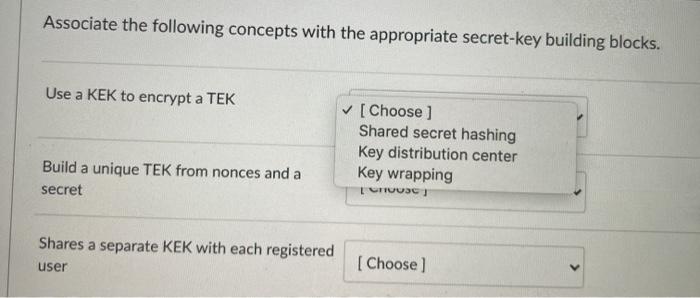
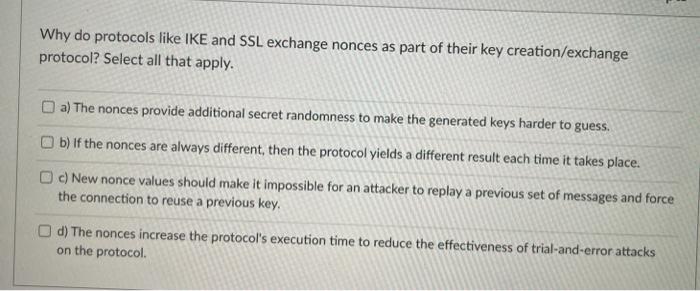
Question: True or False? When replacing crypto keys, they must be all replaced 1 month at a time. True O False Which of the following security
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


