Question: 2. (15 points) User Authentication. (a) (7 points) Consider the following proposed authentication protocol between Alice and Bob based on symmetric encryption with a trusted
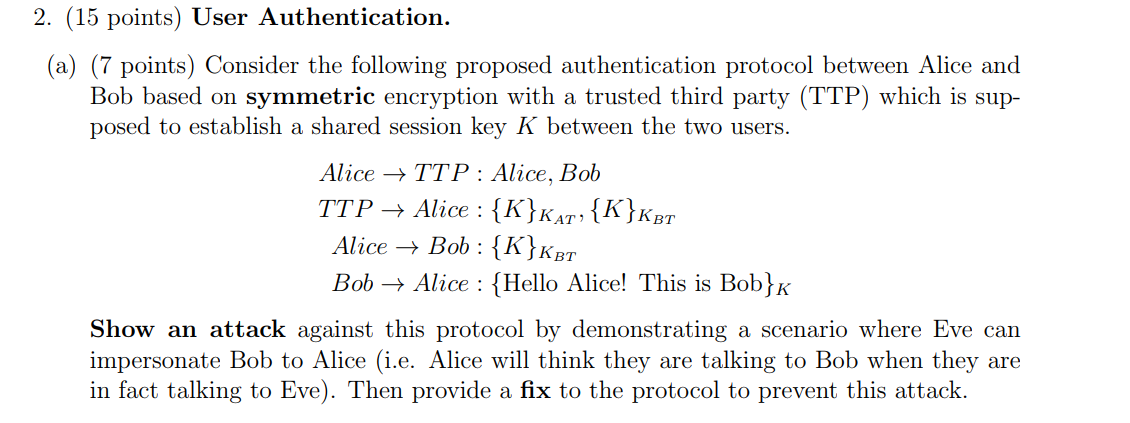
2. (15 points) User Authentication. (a) (7 points) Consider the following proposed authentication protocol between Alice and Bob based on symmetric encryption with a trusted third party (TTP) which is sup- posed to establish a shared session key K between the two users. Alice + TTP: Alice, Bob TTP + Alice : {K}KAT, {K}KBT Alice + Bob : {K}KBT Bob Alice : {Hello Alice! This is Bob}K Show an attack against this protocol by demonstrating a scenario where Eve can impersonate Bob to Alice (i.e. Alice will think they are talking to Bob when they are in fact talking to Eve). Then provide a fix to the protocol to prevent this attack
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


