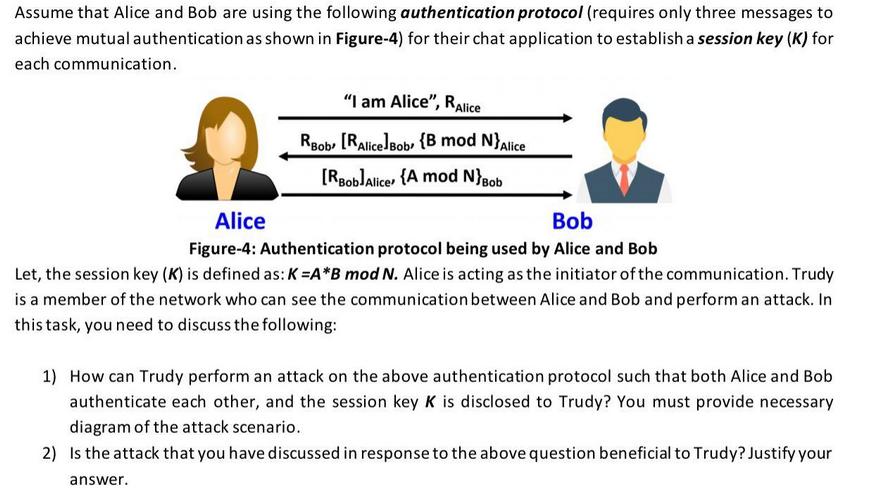
Assume that Alice and Bob are using the following authentication protocol (requires only three messages to...
Fantastic news! We've Found the answer you've been seeking!
Question:
Transcribed Image Text:
Assume that Alice and Bob are using the following authentication protocol (requires only three messages to achieve mutual authentication as shown in Figure-4) for their chat application to establish a session key (K) for each communication. "I am Alice", RAlice RBob [RAlice]Bob (B mod N}Alice [RBob]Alice {A mod N}Bob Alice Bob Figure-4: Authentication protocol being used by Alice and Bob Let, the session key (K) is defined as: K=A*B mod N. Alice is acting as the initiator of the communication. Trudy is a member of the network who can see the communication between Alice and Bob and perform an attack. In this task, you need to discuss the following: 1) How can Trudy perform an attack on the above authentication protocol such that both Alice and Bob authenticate each other, and the session key K is disclosed to Trudy? You must provide necessary diagram of the attack scenario. 2) Is the attack that you have discussed in response to the above question beneficial to Trudy? Justify your answer. Assume that Alice and Bob are using the following authentication protocol (requires only three messages to achieve mutual authentication as shown in Figure-4) for their chat application to establish a session key (K) for each communication. "I am Alice", RAlice RBob [RAlice]Bob (B mod N}Alice [RBob]Alice {A mod N}Bob Alice Bob Figure-4: Authentication protocol being used by Alice and Bob Let, the session key (K) is defined as: K=A*B mod N. Alice is acting as the initiator of the communication. Trudy is a member of the network who can see the communication between Alice and Bob and perform an attack. In this task, you need to discuss the following: 1) How can Trudy perform an attack on the above authentication protocol such that both Alice and Bob authenticate each other, and the session key K is disclosed to Trudy? You must provide necessary diagram of the attack scenario. 2) Is the attack that you have discussed in response to the above question beneficial to Trudy? Justify your answer. Assume that Alice and Bob are using the following authentication protocol (requires only three messages to achieve mutual authentication as shown in Figure-4) for their chat application to establish a session key (K) for each communication. "I am Alice", RAlice RBob [RAlice]Bob (B mod N}Alice [RBob]Alice {A mod N}Bob Alice Bob Figure-4: Authentication protocol being used by Alice and Bob Let, the session key (K) is defined as: K=A*B mod N. Alice is acting as the initiator of the communication. Trudy is a member of the network who can see the communication between Alice and Bob and perform an attack. In this task, you need to discuss the following: 1) How can Trudy perform an attack on the above authentication protocol such that both Alice and Bob authenticate each other, and the session key K is disclosed to Trudy? You must provide necessary diagram of the attack scenario. 2) Is the attack that you have discussed in response to the above question beneficial to Trudy? Justify your answer. Assume that Alice and Bob are using the following authentication protocol (requires only three messages to achieve mutual authentication as shown in Figure-4) for their chat application to establish a session key (K) for each communication. "I am Alice", RAlice RBob [RAlice]Bob (B mod N}Alice [RBob]Alice {A mod N}Bob Alice Bob Figure-4: Authentication protocol being used by Alice and Bob Let, the session key (K) is defined as: K=A*B mod N. Alice is acting as the initiator of the communication. Trudy is a member of the network who can see the communication between Alice and Bob and perform an attack. In this task, you need to discuss the following: 1) How can Trudy perform an attack on the above authentication protocol such that both Alice and Bob authenticate each other, and the session key K is disclosed to Trudy? You must provide necessary diagram of the attack scenario. 2) Is the attack that you have discussed in response to the above question beneficial to Trudy? Justify your answer.
Expert Answer:

Related Book For 

Discrete Mathematics and Its Applications
ISBN: 978-0073383095
7th edition
Authors: Kenneth H. Rosen
Posted Date:
Students also viewed these computer network questions
-
Fox Co. purchases land on January 1 of Year 1 and issues a 3-year, $70,000 zero-interest-bearing note as payment. The market rate is 10%, and Fox Co. uses the effective interest method to amortize...
-
Alice and Bob are employees of two different financial investment companies. Alice works for the S&M investment funds that operates in Melbourne and Bob works for MK superfunds that operates in...
-
Case Study: Quick Fix Dental Practice Technology requirements Application must be built using Visual Studio 2019 or Visual Studio 2017, professional or enterprise. The community edition is not...
-
Problem 8-46 (LO. 2, 4, 9) Dennis Harding is considering acquiring a new automobile that he will use 100% for business in the subsequent year. The purchase price of the automobile would be $54,500....
-
In the planetary gear system shown, the radius of gears A, B, C, and D is 30 mm and the radius of the outer gear E is 90 mm. Knowing that gear E has an angular velocity of 180 rpm clockwise and that...
-
Imagine that you are a web designer at a consulting firm. In this role, you will attempt to win a contract to perform a complete website redesign for a local spa. Your potential client's website was...
-
Prepare a document flowchart to reflect how ANGIC Insurance Company processes its casualty claims. The process begins when the claims department receives a notice of loss from a claimant. Claims...
-
The mean cost of domestic airfares in the United States rose to an all-time high of $385 per ticket (Bureau of Transportation Statistics website, November 2, 2012). Airfares were based on the total...
-
13. You are scheduled to receive $20,000 in two years.When you receive it, you will invest it for six more years at 8.4% per year.How much will you have in eight years? (Show your answer as a...
-
The previous year was Amys first year of operating the bookstore. Amy and Ken elected to carry forward a $4,752 net operating loss from the first year of business into 2015. (Note: Net operating...
-
At the end of December, a business has accrued $1,450 of interest on a loan, on which it will not make another payment until the next year. The adjusting entry necessary would be journalized as a...
-
Determine how much needs to be invested if you want to end up with $5000 in interest after 7 years of simple interest at 1.8% APR. Starting investment= 39682.54 dollars. Your answer must be accurate...
-
1. Write a VHDL Program for 1x4 Demultiplexer using two 1x2 Demultiplexer shown below using structural modelling. I 1x2 S 1x2 1x2 .Yo Y So Select Input Input S(1) S(0) F 00 (0) 01 y(1) 10 (2) 11 (3)...
-
What is the "Consumer Behavior and Marketing Mix" and why is it so important in strategy formulation and implementation?
-
What was Iris Inc.'s earnings before interest and taxes (EBIT)? Cost of good 320 Depreciation expense 35 Interest Expense 20 Operating Expense (excluding depreciation) 115 Sales 800
-
It is March 2017, and you were recently hired as a financial analyst at the private equity group Silver Capital Partners. Your boss tells you that he has heard that the management of Panera Bread, a...
-
Why is Benchmarking against industry standards and competitors important in financial strategic analysis using ratios?
-
Suppose that a flow network G = (V, E) violates the assumption that the network contains a path s t for all vertices V. Let u be a vertex for which there is no path s u t. Show that there must...
-
a) What is the difference between an r-combination and an r-permutation of a set with n elements? b) Derive an equation that relates the number of r-combinations and the number of r-permutations of a...
-
Adapt the proof that there are infinitely many primes (Theorem 3 in Section 4.3) to show that are infinitely many primes in the arithmetic progression 6k + 5, k = 1, 2, . . ..
-
Construct a truth table for each of these compound propositions. a) (p q) (p q) b) (p q) (p q) c) (p q) (p q) d) (p q) (p q) e) (p q) (p r) f) (p q) (p q)
-
Anderson Company must evaluate two capital expenditure proposals. fin Andersons hurdle rate is 12%. Data for the two proposals follow. Using net present value analysis, which proposal is the more...
-
Lakeland Company is considering the purchase of equipment for \($150,000\) The 4 equipment will expand the Companys production and increase revenue by \($40,000\) per year. Annual cash operating...
-
Assuming that money is worth 10%, compute the present value of 1.\($7,000\) received 15 years from today. 2.The right to inherit \($1,000,000\) 14 years from now. 3.The right to receive \($1,000\) at...

Study smarter with the SolutionInn App


