Question: Binary Bomb. I'm currently in phase 2 and its been 2 days struggling to find the 6 numbers to diffuse the bomb. Please help and
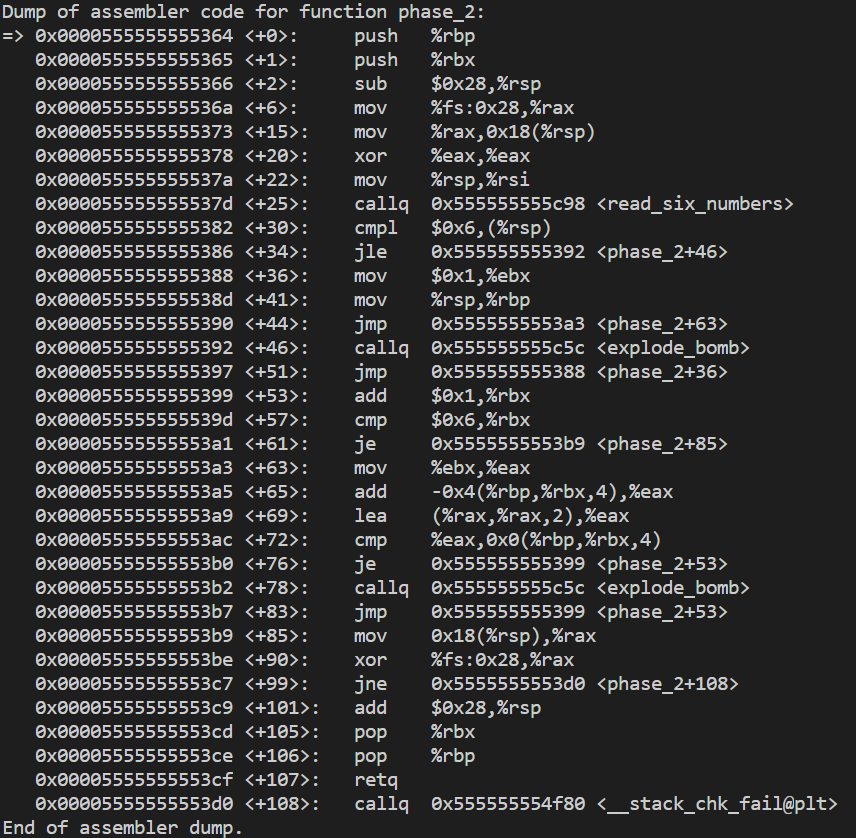
Binary Bomb. I'm currently in phase 2 and its been 2 days struggling to find the 6 numbers to diffuse the bomb.
Please help and explain your steps
Thank you in advance.
#include
#include
#include "support.h"
#include "phases.h"
/*
* Note to self: Remember to erase this file so my victims will have no
* idea what is going on, and so they will all blow up in a
* spectaculary fiendish explosion. -- Dr. Evil
*/
FILE *infile;
int main(int argc, char *argv[])
{
char *input;
/* Note to self: remember to port this bomb to Windows and put a
* fantastic GUI on it. */
/* When run with no arguments, the bomb reads its input lines
* from standard input. */
if (argc == 1) {
infile = stdin;
}
/* When run with one argument
* until EOF, and then switches to standard input. Thus, as you
* defuse each phase, you can add its defusing string to
* avoid having to retype it. */
else if (argc == 2) {
if (!(infile = fopen(argv[1], "r"))) {
printf("%s: Error: Couldn't open %s ", argv[0], argv[1]);
exit(8);
}
}
/* You can't call the bomb with more than 1 command line argument. */
else {
printf("Usage: %s [
exit(8);
}
/* Do all sorts of secret stuff that makes the bomb harder to defuse. */
initialize_bomb();
printf("Welcome to my fiendish little bomb. You have 6 phases with ");
printf("which to blow yourself up. Have a nice day! ");
/* Hmm... Six phases must be more secure than one phase! */
input = read_line(); /* Get input */
phase_1(input); /* Run the phase */
phase_defused(); /* Drat! They figured it out!
* Let me know how they did it. */
printf("Phase 1 defused. How about the next one? ");
/* The second phase is harder. No one will ever figure out
* how to defuse this... */
input = read_line();
phase_2(input);
phase_defused();
printf("That's number 2. Keep going! ");
/* I guess this is too easy so far. Some more complex code will
* confuse people. */
input = read_line();
phase_3(input);
phase_defused();
printf("Halfway there! ");
/* Oh yeah? Well, how good is your math? Try on this saucy problem! */
input = read_line();
phase_4(input);
phase_defused();
printf("So you got that one. Try this one. ");
/* Round and 'round in memory we go, where we stop, the bomb blows! */
input = read_line();
phase_5(input);
phase_defused();
printf("Good work! On to the next... ");
/* This phase will never be used, since no one will get past the
* earlier ones. But just in case, make this one extra hard. */
input = read_line();
phase_6(input);
phase_defused();
/* Wow, they got it! But isn't something... missing? Perhaps
* something they overlooked? Mua ha ha ha ha! */
return 0;
}
by the way the answers is not 1 2 ..................
Shouldnt the number start with 6 since the first Cmpl statement is making sure that the first inout is larger than 6.
jmp Dump OT assembler code for function phase 2: => exe800555555555364 : sub $0x28,%rsp Ox000055555555536a : mov %fs: 0x28,%rax ex0000555555555373 : xor %eax, %eax Ox000055555555537a : mov %rsp,%rsi exe00055555555537d : callq_0x555555555c98
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


