Question: Code a.Primarily a black hat (destructive) activity. White hat (constructive) review thinking drives security requirements, and black hat thinking in the form of attack patterns
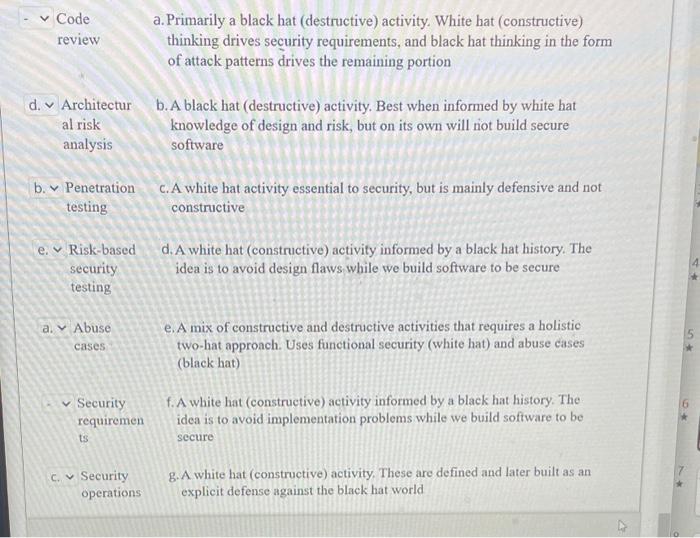
Code a.Primarily a black hat (destructive) activity. White hat (constructive) review thinking drives security requirements, and black hat thinking in the form of attack patterns drives the remaining portion d. Architectur b. A black hat (destructive) activity. Best when informed by white hat al risk knowledge of design and risk, but on its own will not build secure analysis software b. V Penetration c. A white hat activity essential to security, but is mainly defensive and not testing constructive e. V Risk-based d. A white hat (constructive) activity informed by a black hat history. The security idea is to avoid design flaws while we build software to be secure testing a. Abuse e. A mix of constructive and destructive activities that requires a holistic cases two-hat approach. Uses functional security (white hat) and abuse cases (black hat) Security f. A white hat (constructive) activity informed by a black hat history. The requiremen idea is to avoid implementation problems while we build software to be ts secure Security g. A white hat (constructive) activity, These are defined and later built as an operations explicit defense against the black hat world
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


