Question: COMPUTER SCIENCE // CRYPTOLOGY In addition to stack-based buffer overflow attacks (i.e., smashing the stack), heap overflows can also be exploited. Consider the following C
COMPUTER SCIENCE // CRYPTOLOGY
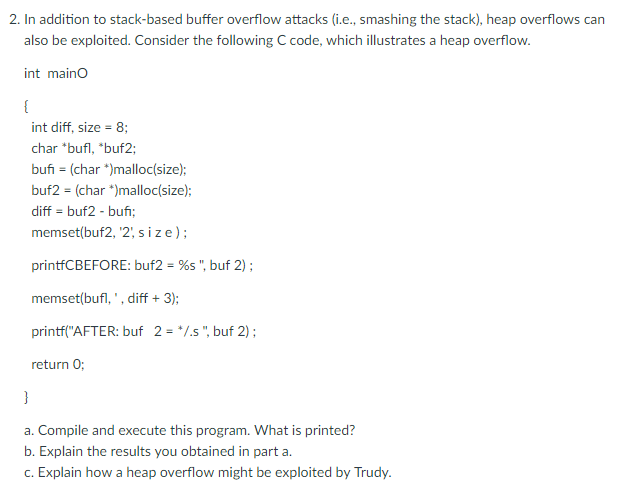
In addition to stack-based buffer overflow attacks (i.e., smashing the stack), heap overflows can also be exploited. Consider the following C code, which illustrates a heap overflow. int main() {int diff, size 8; char *buf, *buf2; buf1 = (char*)malloc (size); buf2 = (char*)malloc (size); diff = buf2 - bufi; memset (buf2, '2', size); printfCBEFORE: buf2 = %s", buf 2); memset (buf, ', diff + 3); print AFTER: buf 2 = */.s" buf 2); return 0} Compile and execute this program. What is printed? Explain the results you obtained in part a. Explain how a heap overflow might be exploited by Trudy
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


