Question: In addition to stack-based buffer overflow attacks (i.e., smashing the stack), integer overflows can also be exploited. Consider the following C code, which illustrates an
In addition to stack-based buffer overflow attacks (i.e., smashing the stack), integer overflows can also be exploited. Consider the following C code, which illustrates an integer overflow [36].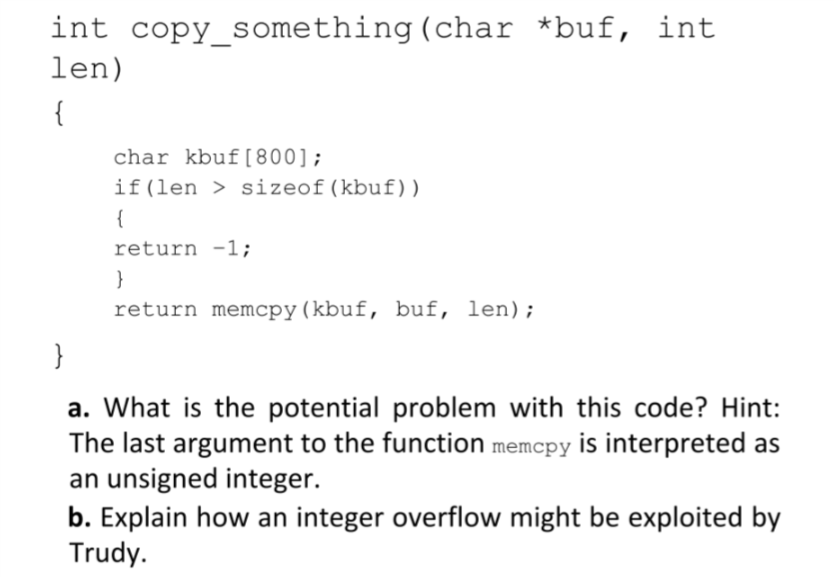
int copy_ len) something (cnar *buf, int char kbuf [800] if (len > sizeof (kbuf)) return-1; return memcpy (kbuf, buf, len); a. What is the potential problem with this code? Hint: The last argument to the function memcpy is interpreted as an unsigned integer. b. Explain how an integer overflow might be exploited by Trudy. int copy_ len) something (cnar *buf, int char kbuf [800] if (len > sizeof (kbuf)) return-1; return memcpy (kbuf, buf, len); a. What is the potential problem with this code? Hint: The last argument to the function memcpy is interpreted as an unsigned integer. b. Explain how an integer overflow might be exploited by Trudy
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


