Question: Following code of release.py : import string import timeit ''' please do not change the following code''' allowed_chars = string.ascii_letters + string.digits from json import
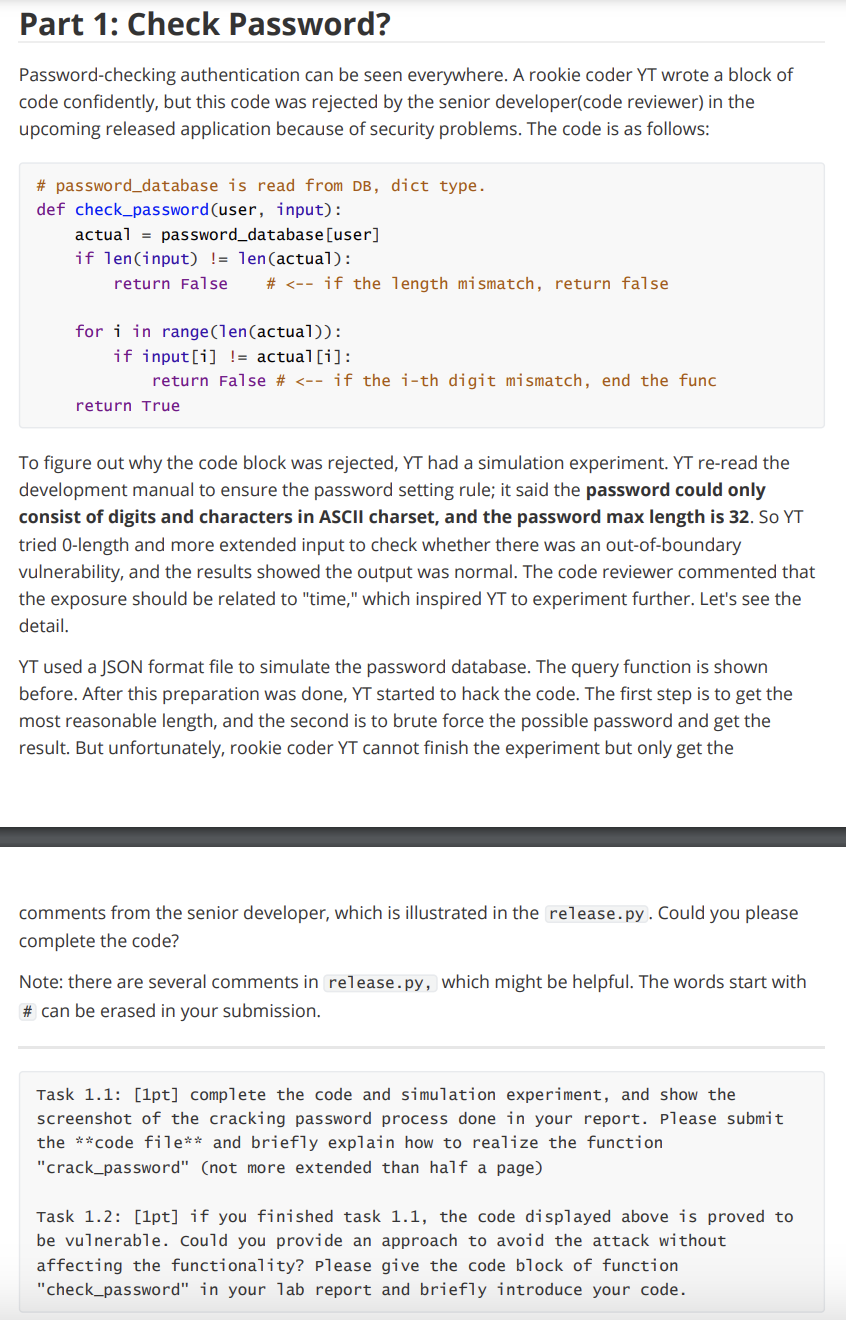
Following code of release.py :
import string import timeit
''' please do not change the following code''' allowed_chars = string.ascii_letters + string.digits from json import load with open("passwords") as f: password_database = load(f)
def check_password(user, input): #
def crack_length(user, max_len=32) -> int: ''' This function will return the most likely length of the password Params: user: the user to crack, str type max_len: the maximum length of the password to try, int type verbose: whether to print the most likely length, bool type Returns: the most likely length of the password, int type ''' most_likely = 0 # most likely length of the password ''' give your code here'''
### check the time of the check_password function for different length of the input ### and find the most likely length of the password ### the length(time) would play a important role in the following crack_password function return most_likely
## Description of the function crack_password: # After you have cracked the length of the password, # you can use this function to crack the password def crack_password(user, length) -> str: ''' This function will return the password Params: user: the user to crack, str type length: the length of the password, int type Returns: the password, str type '''
''' give your code here''' ### 1. init a string with the length of the password guess_passwd = "" # change the value ### 2. use a loop to brute force iterate through the password length \ # and use the check_password function to check if the password is correct.
# IMPORTANT: The condition of ending the loop is the return value is True # IMPORTANT: Please note that iterating and storing the correct password string
### 3. if the password is correct, return the password
def main(): length = crack_length(user="ierg4300") print(f"the most likely length should be: {length}")
password = crack_password(user="ierg4300", length=length) print(f"password:'{password}'")
if __name__ == '__main__': main()
### Here are HINTs for time calculation # 1. Python has built-in modules, like time, datetime, etc. If you choose these modules, please focus on the precise. # We recommend using the timeit module to calculate the time. The official document is here: https://docs.python.org/3/library/timeit.html # 2. The timeit module has a repeat method, which can repeat the execution of the code several times and return a list of times. # Why we need the repeat method: it can reduce the influence of the fluctuation of other factors, like CPU scheduling. # you also can realize the repeat method by yourself, but it is not necessary.
Password-checking authentication can be seen everywhere. A rookie coder YT wrote a block of code confidently, but this code was rejected by the senior developer(code reviewer) in the upcoming released application because of security problems. The code is as follows: \# password_database is read from DB, dict type. def check_password(user, input): actual = password_database [user] if 1 en(input) != len(actual): return False \#i in range(len(actual)): if input [i]!= actual [i]: return False \#i th digit mismatch, end the func return True To figure out why the code block was rejected, YT had a simulation experiment. YT re-read the development manual to ensure the password setting rule; it said the password could only consist of digits and characters in ASCII charset, and the password max length is 32. So YT tried 0-length and more extended input to check whether there was an out-of-boundary vulnerability, and the results showed the output was normal. The code reviewer commented that the exposure should be related to "time," which inspired YT to experiment further. Let's see the detail. YT used a JSON format file to simulate the password database. The query function is shown before. After this preparation was done, YT started to hack the code. The first step is to get the most reasonable length, and the second is to brute force the possible password and get the result. But unfortunately, rookie coder YT cannot finish the experiment but only get the comments from the senior developer, which is illustrated in the release.py. Could you please complete the code? Note: there are several comments in release.py, which might be helpful. The words start with \# can be erased in your submission. Task 1.1: [1pt] complete the code and simulation experiment, and show the screenshot of the cracking password process done in your report. Please submit the **code file** and briefly explain how to realize the function "crack_password" (not more extended than half a page) Task 1.2: [1pt] if you finished task 1.1, the code displayed above is proved to be vulnerable. Could you provide an approach to avoid the attack without affecting the functionality? Please give the code block of function "check_password" in your lab report and briefly introduce your code
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


