Question: Identify Controls: Security Governance Look at each Subcategory and decide if it is adminstrative, physical, technical, or artifact control. Once you identify the control in
Identify Controls: Security Governance
Look at each Subcategory and decide if it is adminstrative, physical, technical, or artifact control. Once you identify the control in the box, you have to declare if it is preventative, detective, or corrective.
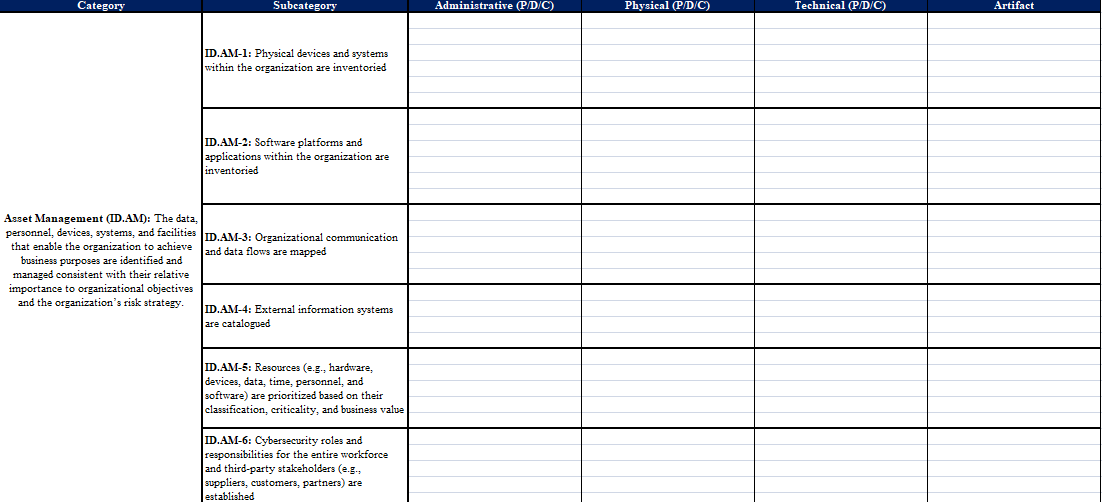
Category Subcategory Administrative (P/D/C) Physical (P/D/C) Technical (P/D/C) Artifact ID.AM-1: Physical devices and systems within the organization are inventoried ID.AM-2: Software platforms and applications within the organization are inventoried Asset Management (ID.AM): The data, personnel, devices, systems, and facilities D.AM-3: Organizational communication that enable the organization to achieve and data flows are mapped business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization's risk strategy. ID.AM-4: External information systems are catalogued ID.AM-5: Resources (e.g., hardware, devices, data, time, personnel, and software) are prioritized based on their classification, criticality, and business value ID.AM-6: Cybersecurity roles and responsibilities for the entire workforce and third-party stakeholders (e.g., suppliers, customers, partners) are established




