Question: information security subject Question 3: Fill in empty cells (9 pts) For each empty cell in the table below, answer whether the defense mechanism listed
information security subject
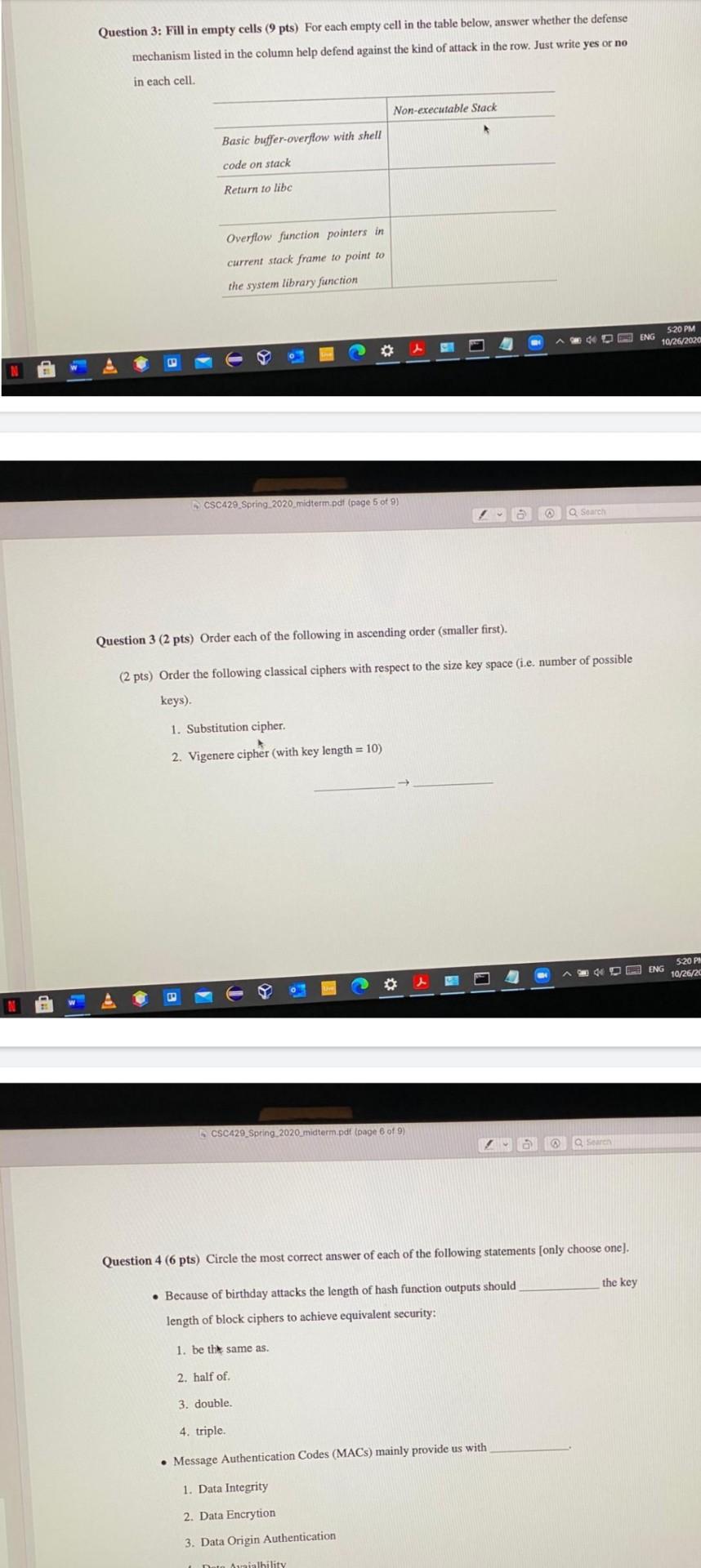
Question 3: Fill in empty cells (9 pts) For each empty cell in the table below, answer whether the defense mechanism listed in the column help defend against the kind of attack in the row. Just write yes or no in each cell. Non-executable Stack Basic buffer-overflow with shell code on stack Return to libc Overflow function pointers in current stack frame to point to the system library function O ENG 5:20 PM 10/26/2020 N CSC429 Spring 2020 midterm.pdf (page 5 of 9) @ Q Search Question 3 (2 pts) Order each of the following in ascending order (smaller first). (2 pts) Order the following classical ciphers with respect to the size key space (i.e. number of possible keys). 1. Substitution cipher. 2. Vigenere cipher (with key length = 10) ENG 520 PM 10/26/20 N CSC429_Spring 2020_midterm.pdf (page 8 of 9) Q Search Question 4 (6 pts) Circle the most correct answer of each of the following statements (only choose one). the key Because of birthday attacks the length of hash function outputs should length of block ciphers to achieve equivalent security: 1. be the same as. 2. half of 3. double 4. triple Message Authentication Codes (MACs) mainly provide us with 1. Data Integrity 2. Data Encrytion 3. Data Origin Authentication Awaialbility
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


