Question: The shellcode and BoF attack layout discussed in the Smashing article can be summarized in the following figure (e.g., Figure 2). However, the size of
The shellcode and BoF attack layout discussed in the Smashing article can be summarized in the following figure (e.g., Figure 2). However, the size of the shellcode is bounded by the size of the buffer to be exploited. In certain cases, the size of the shellcode might be too large to be put into the buffer to be exploited. Please propose one solution to solve this challenge (you should plot the stack layout of your solution.)
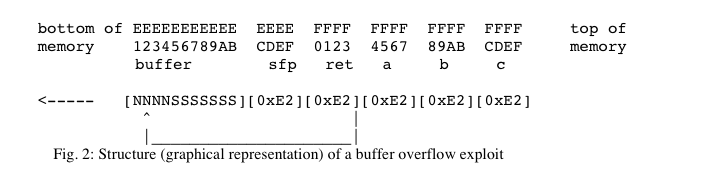
bottom of EEEEEEEEEEE EEEE FFFF FFFF FFFF FFFF memory123456789AB CDEF 0123 4567 89AB CDEF top of memory buffer sfp ret a
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


