Question: 1. (30 Points) Consider the code segment in RISC-V which is similar to LEGv8 fld fo, 0(x0) load f0 from address 0+x0 fld fmult f2,
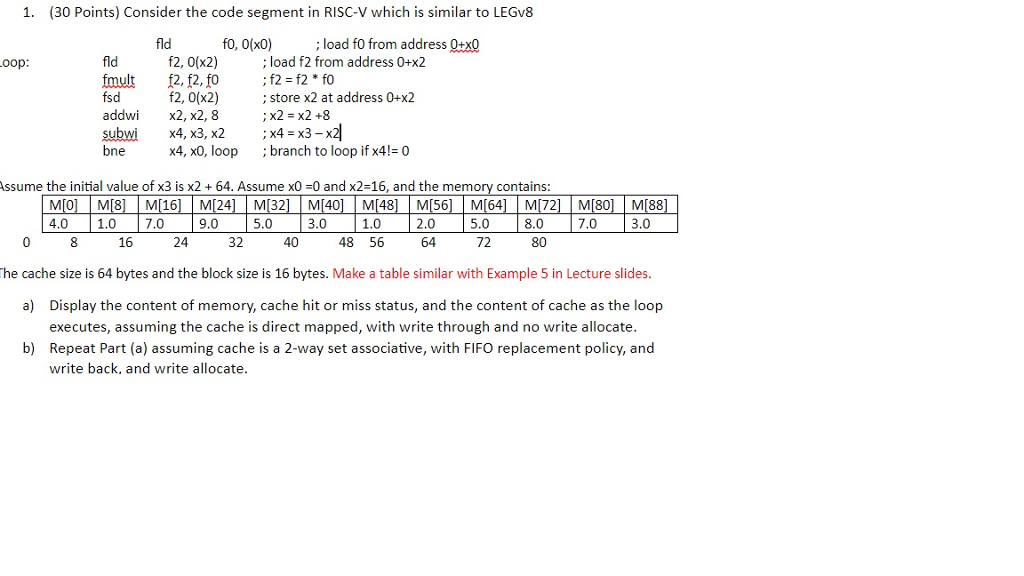
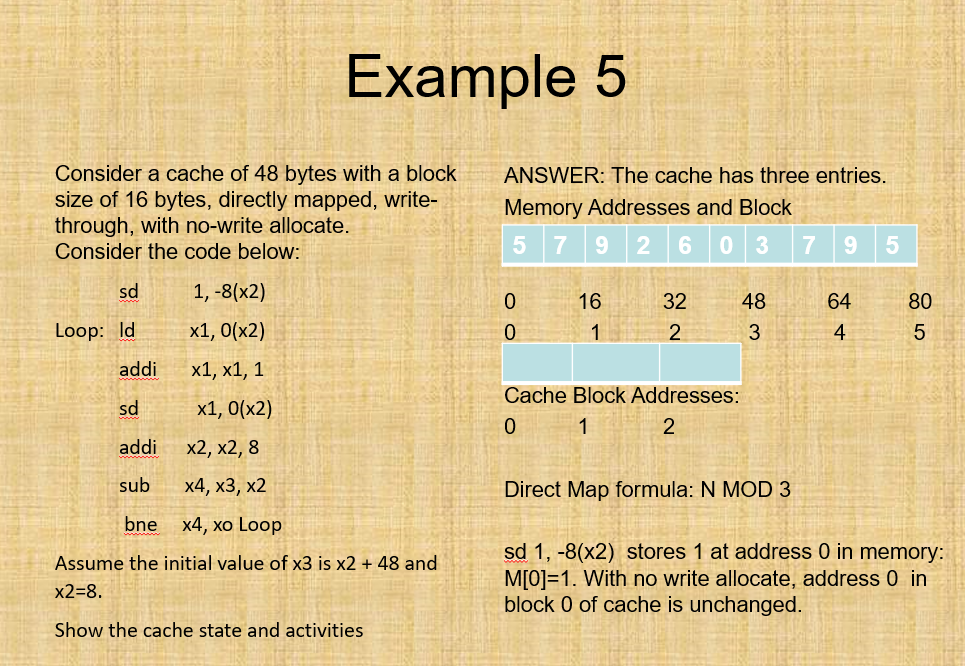
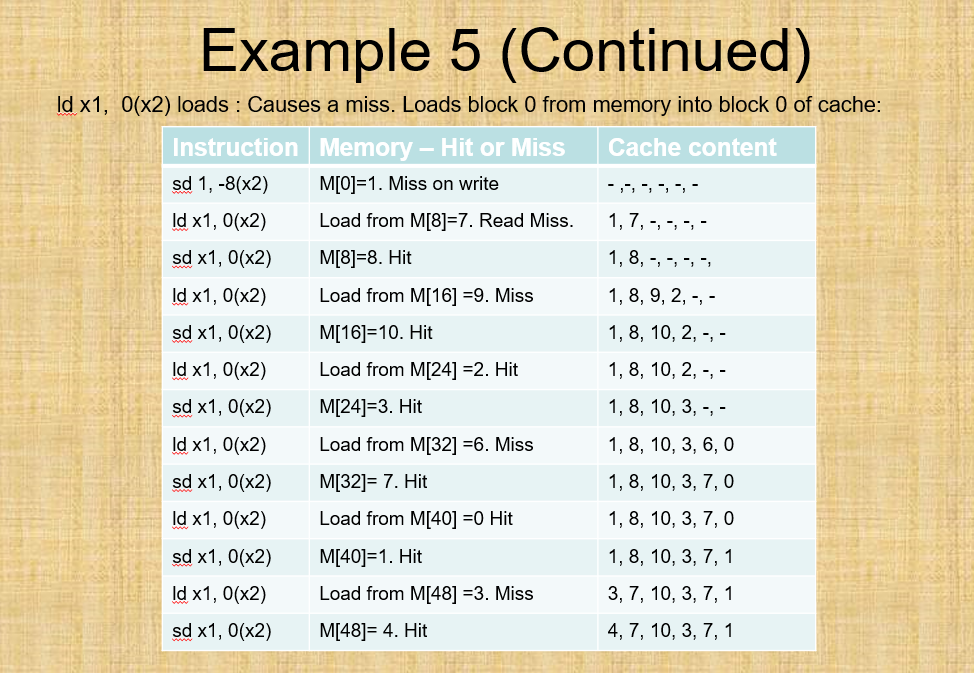
1. (30 Points) Consider the code segment in RISC-V which is similar to LEGv8 fld fo, 0(x0) load f0 from address 0+x0 fld fmult f2, f2,fo;f2-f2* fo fsd addwix2, x2, 8 subm x4, x3, x2 ;x4-x3-x4 bne oop f2, 0(x2) ; load f2 from address 0+x2 f2, 0(x2) ; store x2 at address 0+x2 ;x2 x2+8 x4, x0, loopbranch to loop if x4!-0 ssume the initial value of x3 is x264. Assume x0 0 and x2-16, and the memory contains: MIol | M[8] | M[16] 4.0 1.0 7.0 | M[24] 9.0 | M[32] 5.0 | M[40] 3.0 | M[481 | M[56] 2.0 64 | M(64] 5.0 72 | MI721 8.0 80 | M[801 7.0 | M188 3.0 16 24 32 40 48 56 he cache size is 64 bytes and the block size is 16 bytes. Make a table similar with Example 5 in Lecture slides. a) Display the content of memory, cache hit or miss status, and the content of cache as the loop executes, assuming the cache is direct mapped, with write through and no write allocate Repeat Part (a) assuming cache is a 2-way set associative, with FIFO replacement policy, and write back, and write allocate b) 1. (30 Points) Consider the code segment in RISC-V which is similar to LEGv8 fld fo, 0(x0) load f0 from address 0+x0 fld fmult f2, f2,fo;f2-f2* fo fsd addwix2, x2, 8 subm x4, x3, x2 ;x4-x3-x4 bne oop f2, 0(x2) ; load f2 from address 0+x2 f2, 0(x2) ; store x2 at address 0+x2 ;x2 x2+8 x4, x0, loopbranch to loop if x4!-0 ssume the initial value of x3 is x264. Assume x0 0 and x2-16, and the memory contains: MIol | M[8] | M[16] 4.0 1.0 7.0 | M[24] 9.0 | M[32] 5.0 | M[40] 3.0 | M[481 | M[56] 2.0 64 | M(64] 5.0 72 | MI721 8.0 80 | M[801 7.0 | M188 3.0 16 24 32 40 48 56 he cache size is 64 bytes and the block size is 16 bytes. Make a table similar with Example 5 in Lecture slides. a) Display the content of memory, cache hit or miss status, and the content of cache as the loop executes, assuming the cache is direct mapped, with write through and no write allocate Repeat Part (a) assuming cache is a 2-way set associative, with FIFO replacement policy, and write back, and write allocate b)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


