Question: 1) Consider the following RISC-V mnemonic machine language program 200 LD 204 SUB 208 SD 20C ADDI X6. X6, S8 210 ADDI X28, X28, 8
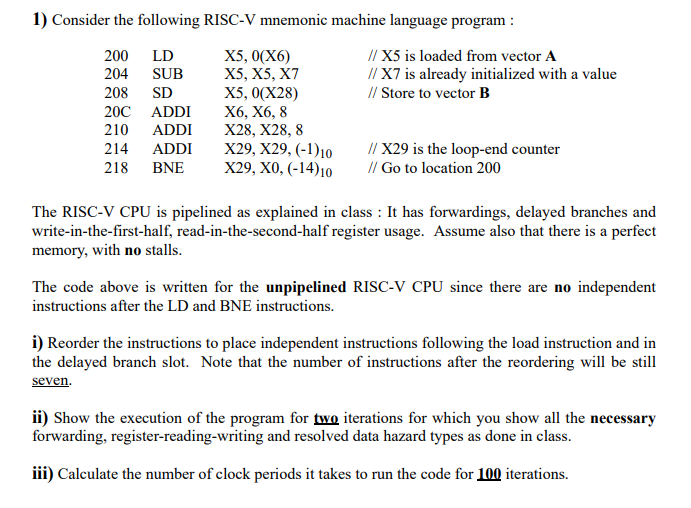
1) Consider the following RISC-V mnemonic machine language program 200 LD 204 SUB 208 SD 20C ADDI X6. X6, S8 210 ADDI X28, X28, 8 214 ADDI X29, X29. (-10 218 BNE X29, X0, (-14)10 X5, 0(X6) X5, X5, X'7 X5, 0(X28) // X5 is loaded from vector A // X7 is already initialized with a value // Store to vector B X29 is the loop-end counter Go to location 200 The RISC-V CPU is pipelined as explained in class : It has forwardings, delayed branches and write-in-the-first-half, read-in-the-second-half register usage. Assume also that there is a perfect memory, with no stalls The code above is written for the unpipelined RISC-V CPU since there are no independent instructions after the LD and BNE instructions. i) Reorder the instructions to place independent instructions following the load instruction and in the delayed branch slot. Note that the number of instructions after the reordering will be still seven ii) show the execution of the program for two iterations for which you show all the necessary forwarding, register-reading-writing and resolved data hazard types as done in class. iii) calculate the number of clock periods it takes to run the code for100 iterations. 1) Consider the following RISC-V mnemonic machine language program 200 LD 204 SUB 208 SD 20C ADDI X6. X6, S8 210 ADDI X28, X28, 8 214 ADDI X29, X29. (-10 218 BNE X29, X0, (-14)10 X5, 0(X6) X5, X5, X'7 X5, 0(X28) // X5 is loaded from vector A // X7 is already initialized with a value // Store to vector B X29 is the loop-end counter Go to location 200 The RISC-V CPU is pipelined as explained in class : It has forwardings, delayed branches and write-in-the-first-half, read-in-the-second-half register usage. Assume also that there is a perfect memory, with no stalls The code above is written for the unpipelined RISC-V CPU since there are no independent instructions after the LD and BNE instructions. i) Reorder the instructions to place independent instructions following the load instruction and in the delayed branch slot. Note that the number of instructions after the reordering will be still seven ii) show the execution of the program for two iterations for which you show all the necessary forwarding, register-reading-writing and resolved data hazard types as done in class. iii) calculate the number of clock periods it takes to run the code for100 iterations
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


