Question: 3) Consider the following RISC-V mnemonic machine language program 400100 LD 400104 LD 400108 LD 40010C ADD 400110 SD 400114 ADDI X12, X12,8 400118 ADDI
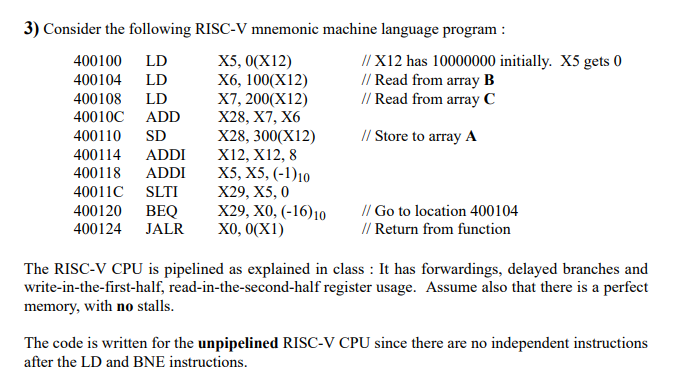

3) Consider the following RISC-V mnemonic machine language program 400100 LD 400104 LD 400108 LD 40010C ADD 400110 SD 400114 ADDI X12, X12,8 400118 ADDI X5, X5, (-D10 40011C SLTI 400120 BEQX29, X0, (-16)10Go to location 400104 400124 JALR X0, 0(XI) X5, 0(X12) X6, 100(X12) X7, 200(X12) X28, X7, X6 X28, 300(X12) // X12 has 10000000 initially. X5 gets 0 // Read from array B // Read from array C // Store to array A X29, X5, 0 / Return from function The RISC-V CPU is pipelined as explained in class : It has forwardings, delayed branches and write-in-the-first-half, read-in-the-second-half register usage. Assume also that there is a perfect memory, with no stalls The code is written for the unpipelined RISC-V CPU since there are no independent instructions after the LD and BNE instructions. 3) Consider the following RISC-V mnemonic machine language program 400100 LD 400104 LD 400108 LD 40010C ADD 400110 SD 400114 ADDI X12, X12,8 400118 ADDI X5, X5, (-D10 40011C SLTI 400120 BEQX29, X0, (-16)10Go to location 400104 400124 JALR X0, 0(XI) X5, 0(X12) X6, 100(X12) X7, 200(X12) X28, X7, X6 X28, 300(X12) // X12 has 10000000 initially. X5 gets 0 // Read from array B // Read from array C // Store to array A X29, X5, 0 / Return from function The RISC-V CPU is pipelined as explained in class : It has forwardings, delayed branches and write-in-the-first-half, read-in-the-second-half register usage. Assume also that there is a perfect memory, with no stalls The code is written for the unpipelined RISC-V CPU since there are no independent instructions after the LD and BNE instructions
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


