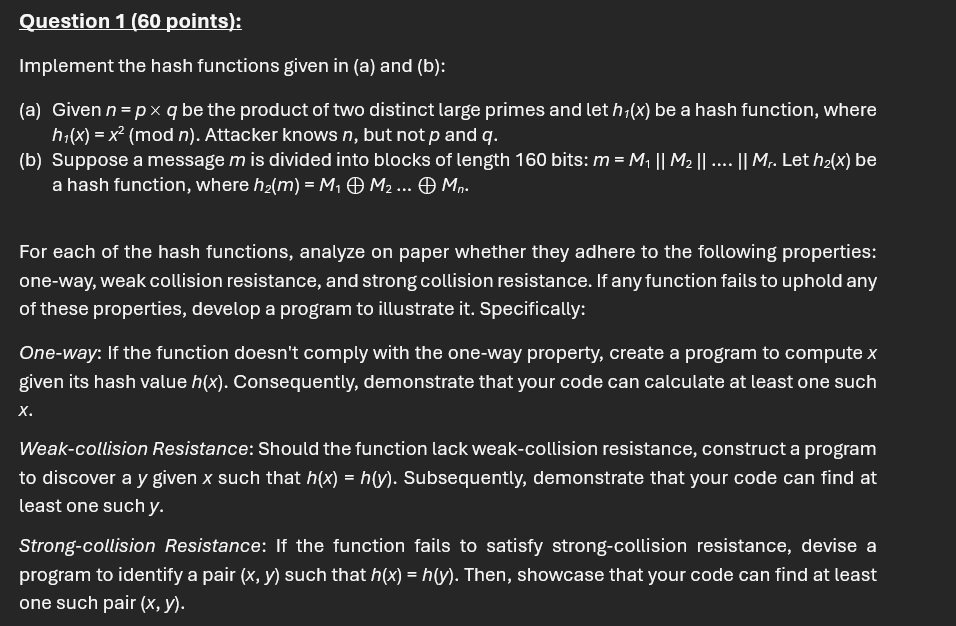
Question: Implement the hash functions given i n ( a ) and ( b ) : ( a ) Given n = p q b e
Implement the hash functions given and :
Given the product two distinct large primes and let a hash function, where Attacker knows but not and
Suppose a message divided into blocks length bits: Let a hash function, where
For each the hash functions, analyze paper whether they adhere the following properties: oneway, weak collision resistance, and strong collision resistance. any function fails uphold any these properties, develop a program illustrate Specifically:
Oneway: the function doesn't comply with the oneway property, create a program compute given its hash value Consequently, demonstrate that your code can calculate least one such
Weakcollision Resistance: Should the function lack weakcollision resistance, construct a program discover given such that Subsequently, demonstrate that your code can find least one such
Strongcollision Resistance: the function fails satisfy strongcollision resistance, devise a program identify a pair such that Then, showcase that your code can find least one such pair
Question points:
Implement the hash functions given and :
Given the product two distinct large primes and let a hash function, where
Attacker knows but not and
Suppose a message divided into blocks length bits: Let
a hash function, where dotso
For each the hash functions, analyze paper whether they adhere the following properties:
oneway, weak collision resistance, and strong collision resistance. any function fails uphold any
these properties, develop a program illustrate Specifically:
Oneway: the function doesn't comply with the oneway property, create a program compute
given its hash value Consequently, demonstrate that your code can calculate least one such
Weakcollision Resistance: Should the function lack weakcollision resistance, construct a program
discover given such that Subsequently, demonstrate that you Pls remember that attacker know nothing about b
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


