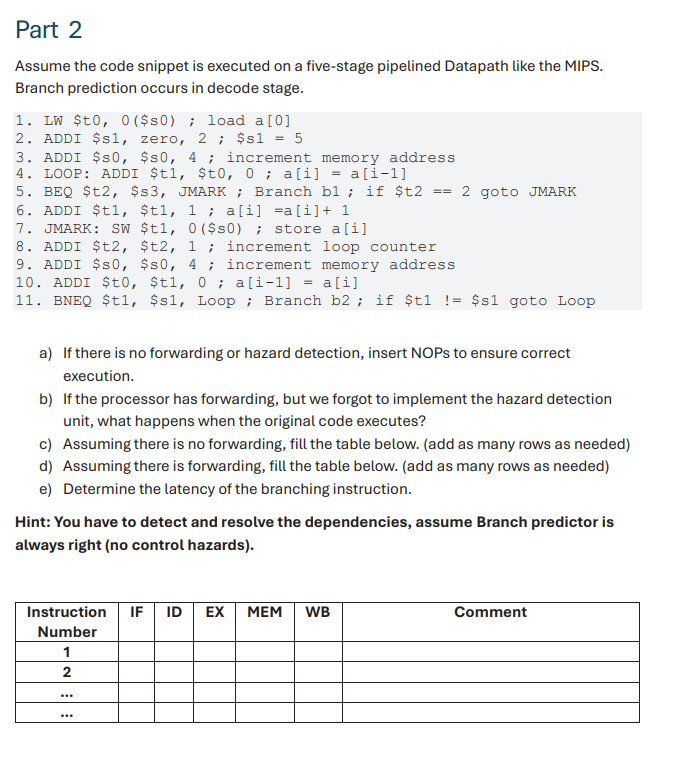
Question: Part 2 Assume the code snippet is executed on a five - stage pipelined Datapath like the MIPS. Branch prediction occurs in decode stage. 1
Part
Assume the code snippet is executed on a fivestage pipelined Datapath like the MIPS. Branch prediction occurs in decode stage.
LW $t$ s ; load a
ADDI $s zero, ; $s
ADDI $s$s; increment memory address
LOOP: ADDI $t$t ; ai ai
BEQ $t$s JMARK ; Branch b ; if $t goto JMARK
ADDI $t$t ; aiai
JMARK: SW $t$ mathrm~s; store ai
ADDI $t$t ; increment loop counter
ADDI $s$s ; increment memory address
ADDI $t$t ; ai ai
BNEQ $t$s Loop ; Branch b ; if $t$s goto Loop
a If there is no forwarding or hazard detection, insert NOPs to ensure correct execution.
b If the processor has forwarding, but we forgot to implement the hazard detection unit, what happens when the original code executes?
c Assuming there is no forwarding, fill the table below. add as many rows as needed
d Assuming there is forwarding, fill the table below. add as many rows as needed
e Determine the latency of the branching instruction.
Hint: You have to detect and resolve the dependencies, assume Branch predictor is always right no control hazards
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


