Question: Please ANSWER all question for thumbs up. Please ANSWER all question for thumbs up. Question 95 of 100 Which principle verifies that the user is
Please ANSWER all question for thumbs up.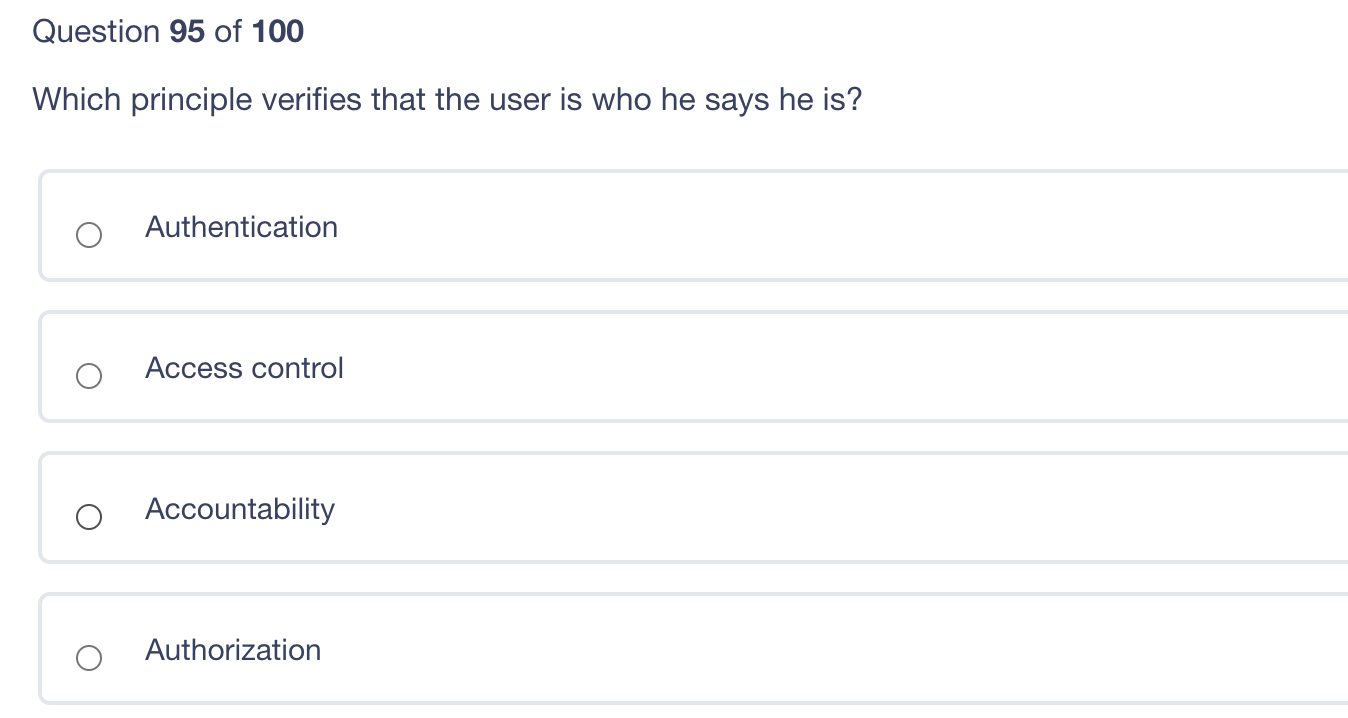
 Please ANSWER all question for thumbs up.
Please ANSWER all question for thumbs up.
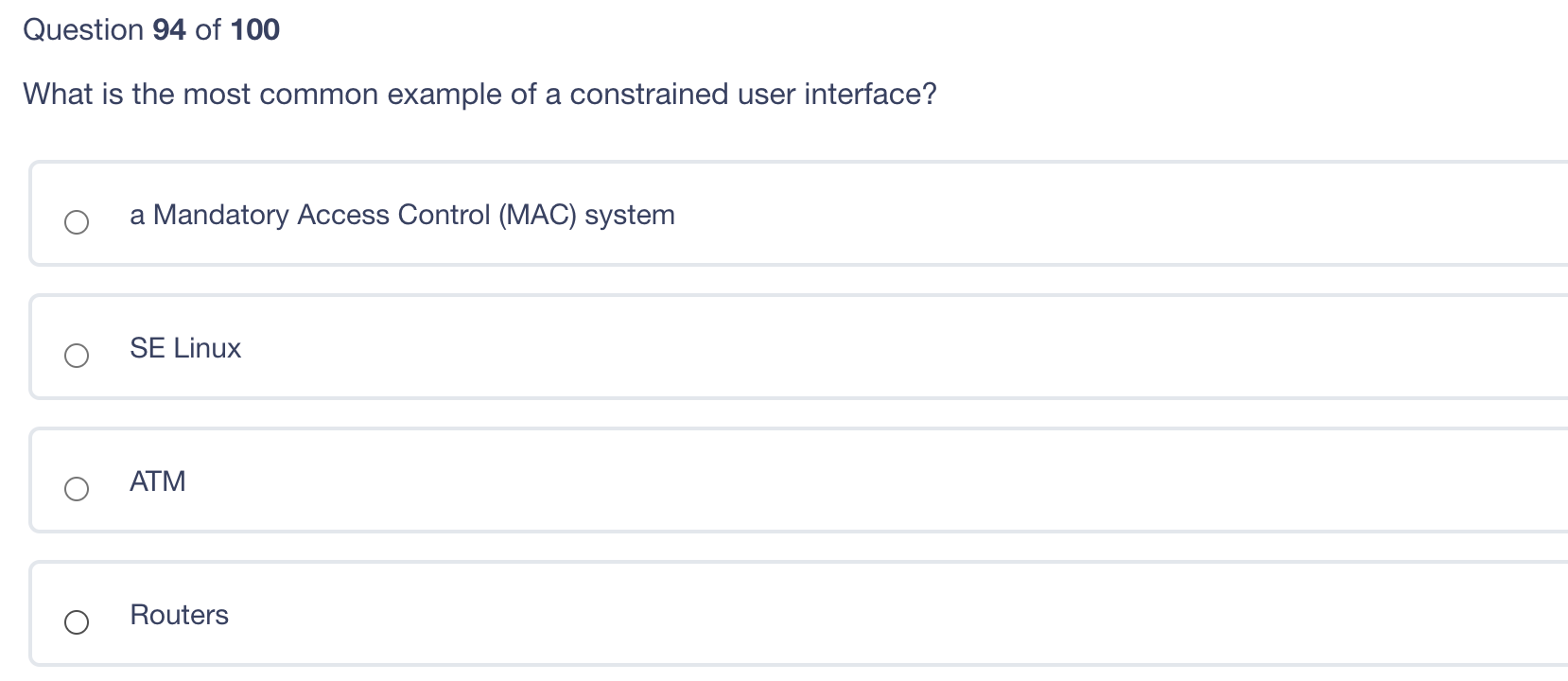
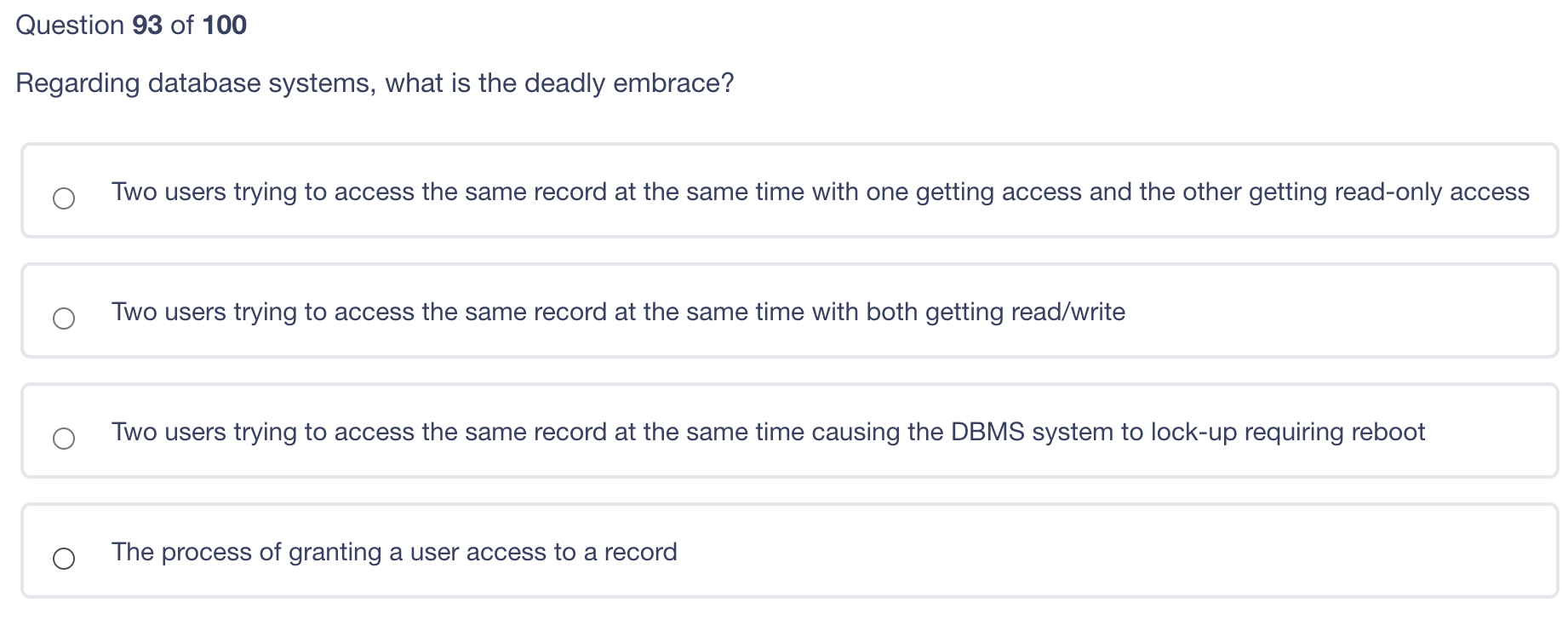
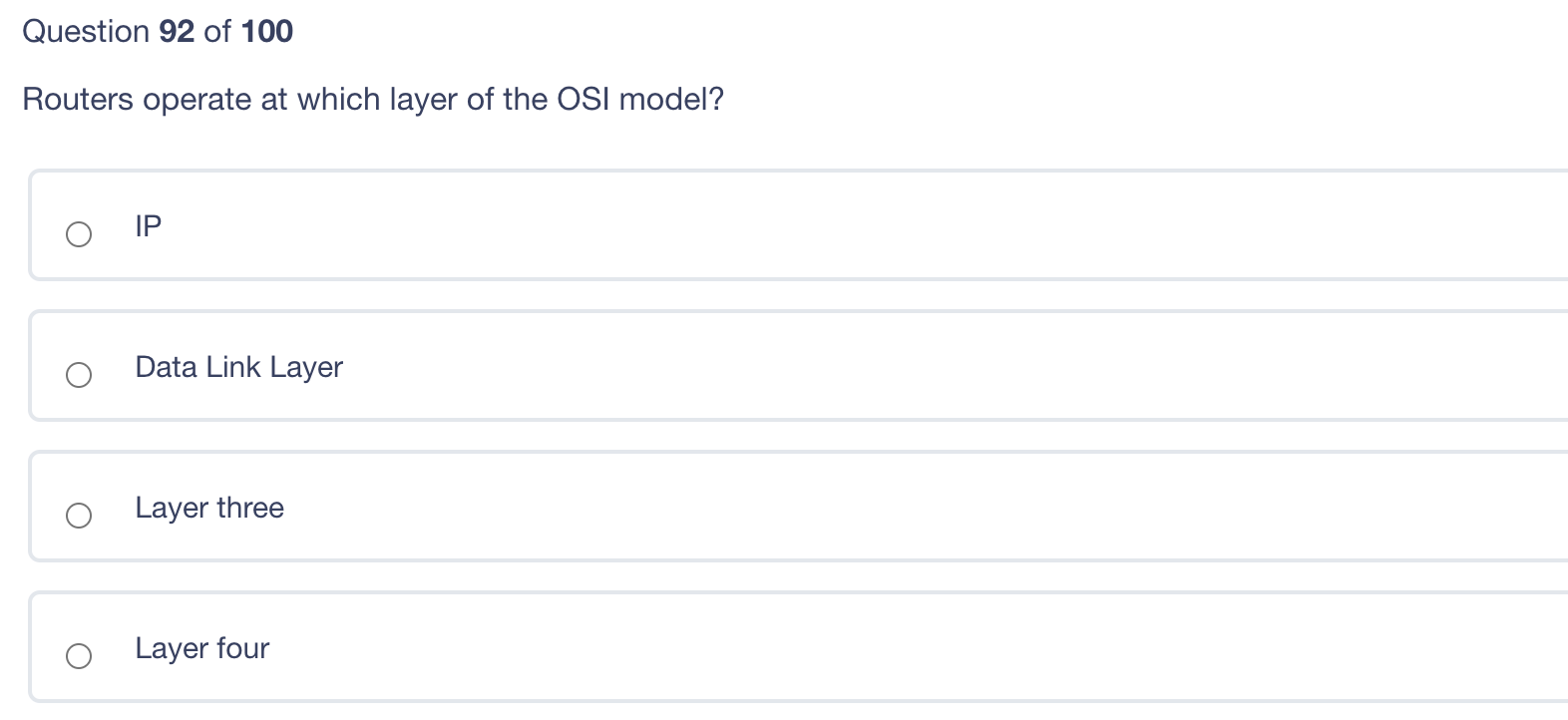
Question 95 of 100 Which principle verifies that the user is who he says he is? Authentication Access control Accountability Authorization Question 94 of 100 What is the most common example of a constrained user interface? a Mandatory Access Control (MAC) system SE Linux ATM Routers Regarding database systems, what is the deadly embrace? Two users trying to access the same record at the same time with one getting access and the other getting read-only access Two users trying to access the same record at the same time with both getting read/write Two users trying to access the same record at the same time causing the DBMS system to lock-up requiring reboot The process of granting a user access to a record Question 92 of 100 Routers operate at which layer of the OSI model? IP Data Link Layer Layer three Layer four Question 91 of 100 What is degaussing? A method for making data impossible to read on CD disks A method for erasing data from hard drives A method used to protect data from accidental destruction Physically destroying the disk
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


