Question: Thx!!! In this question you will double encrypt/decrypt your first and last name (separated by a ') using public and symmetric key approaches (if you
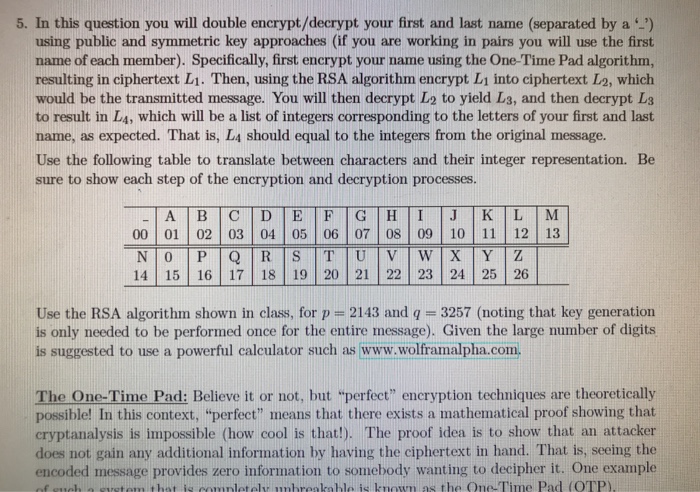

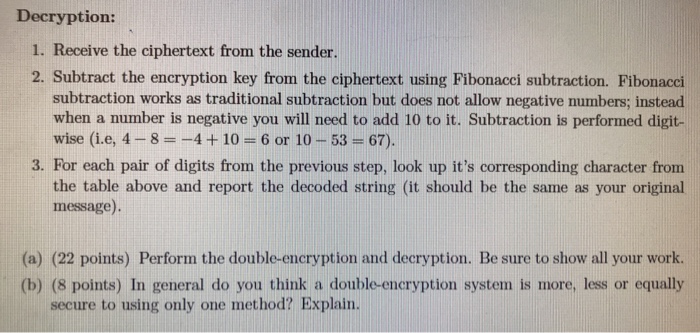
In this question you will double encrypt/decrypt your first and last name (separated by a ') using public and symmetric key approaches (if you are working in pairs you will use the first name of each member). Specifically, first encrypt your name using the One-Time Pad algorithm, resulting in ciphertext L1. Then, using the RSA algorithm encrypt L1 into ciphertext L2, which would be the transmitted message. You will then decrypt I2 to yield Ls, and then decrypt L3 to result in Ls, which will be a list of integers corresponding to the letters of your first and last name, as expected. That is, L4 should equal to the integers from the original message. Use the following table to translate between characters and their integer representation. Be sure to show each step of the encryption and decryption processes. A | B |C |D | E |F |G | H | | |J |K | L |M 00 01 02 03 04 05 06 07 08 09 10 11 12 13 14 1516 17 18 19 20 21 22 23 24 25 26 Use the RSA algorithm shown in class, for p 2143 and q 3257 (noting that key generation is only needed to be performed once for the entire message). Given the large number of digits suggested to use a powerful calculator such as www.wolframalpha.com. The One-Time Pad: Believe it or not, but "perfect" encryption techniques are theoretically ible! In this context, "perfect" means that there exists a mathematical proof showing that cryptanalysis is impossible (how cool is that!). The proof idea is to show that an attacker does not gain any additional information by having the ciphertext in hand. That is, seeing the encoded message provides zero information to somebody wanting to decipher it. One example letelw mbreakable is known the Qne-Time Pad (OTP)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


