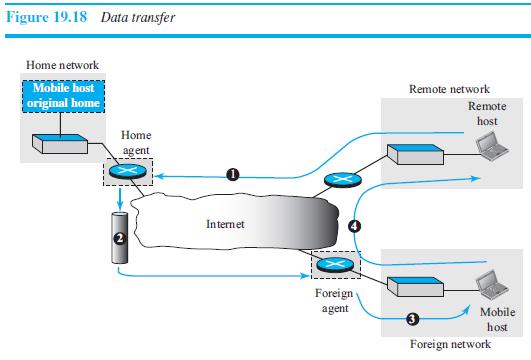
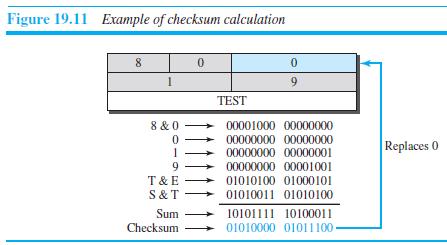
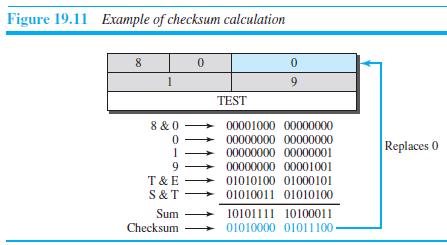
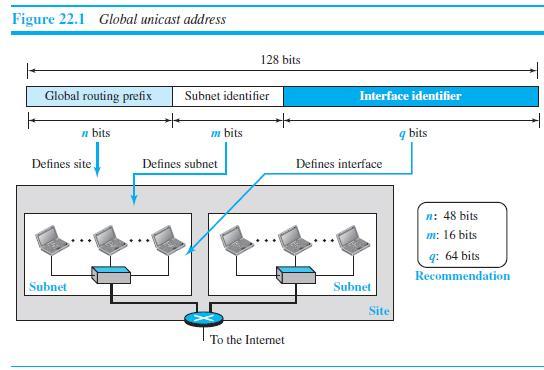
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()


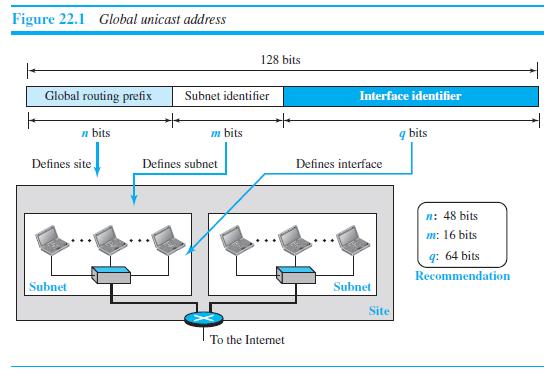
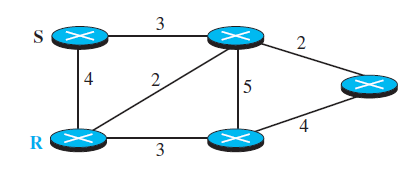
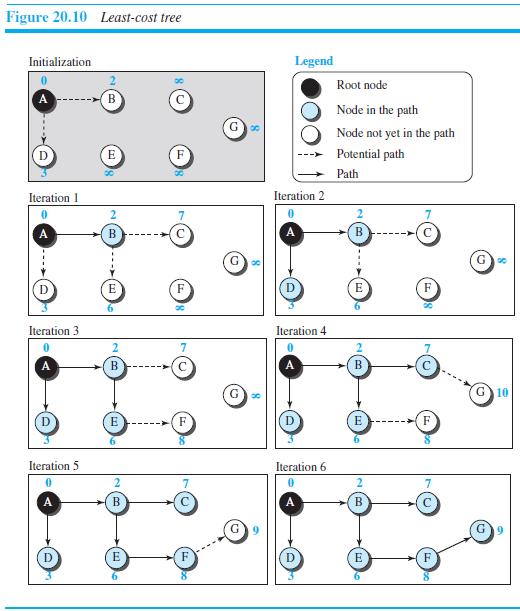
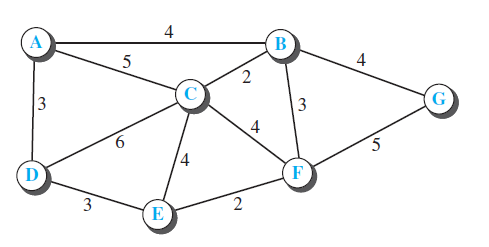
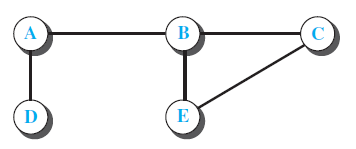
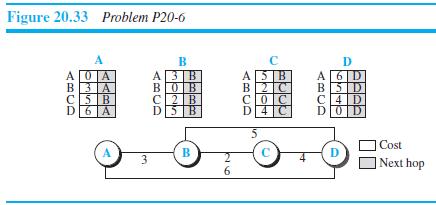
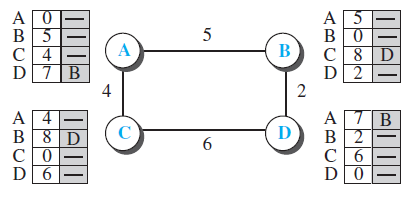
![Table 20.3 Path-vector algorithm for a node 1 Path_Vector_Routing ( ) 2 { // Initialization for (y = 1 to N) 3 { if (y is myself) Path[y] = myself else if (y is a neighbor) 9. Path[y] = myself + neighbor node 10 else 11 Path[y] = empty 12](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1607/4/8/9/3825fd057660847a1607489381626.jpg)


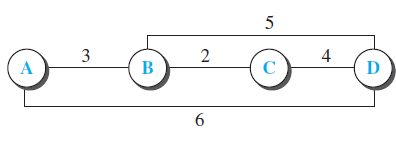
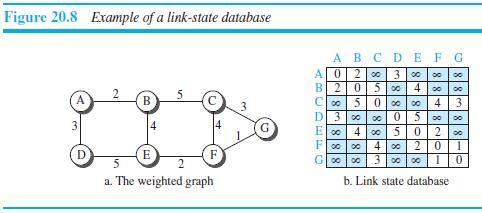
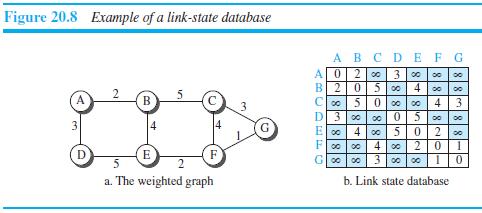
![Distance_Vector_Routing ( ) // Initialize (create initial vectors for the node) D[myself] = 0 4-](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1544/8/0/0/3205c13c8405b9ac1544782874654.jpg)

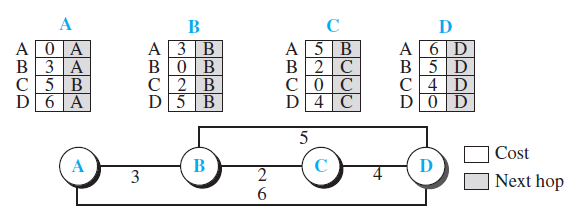
![B D C|0 D] 6 D|0 ABCD + bo ABCD ABCD](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1607/4/8/9/0625fd05626de53c1607489062886.jpg)
![B D C|0 D] 6 D|0 ABCD + bo ABCD ABCD](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1607/4/8/9/0505fd0561ace8721607489050235.jpg)