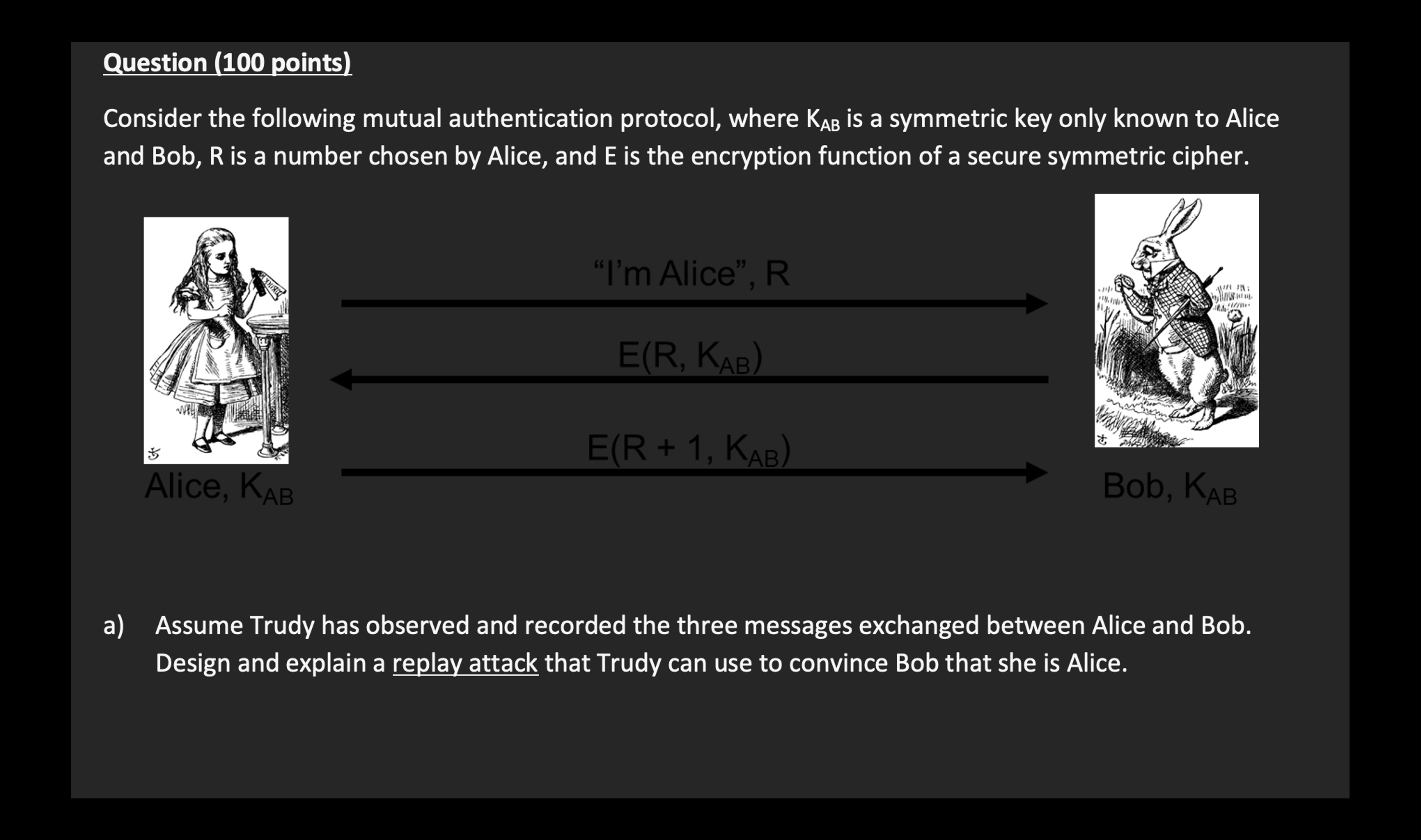
Question: Question ( 1 0 0 points ) Consider the following mutual authentication protocol, where K A B is a symmetric key only known to Alice
Question points
Consider the following mutual authentication protocol, where is a symmetric key only known to Alice
and Bob, is a number chosen by Alice, and is the encryption function of a secure symmetric cipher.
Im Alice",
Alice,
a Assume Trudy has observed and recorded the three messages exchanged between Alice and Bob.
Design and explain a replay attack that Trudy can use to convince Bob that she is Alice.
b Assume Trudy knows this protocol but is not able to record and observe the three messages exchanged between Alice and Bob. Design and explain a reflection attack that Trudy can use to convince Bob that she is Alice.
Hint: One step is: Trudy suspends the initial connection, and opens a new connection and send some number related to R to Bob, Bob replies with some information. Such information will be useful for Trudy
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


