Question: 94.1 The following mutual authentication protocol is based on a shared symmetric key KAB. It can be shown that Trudy can attack the protocol to
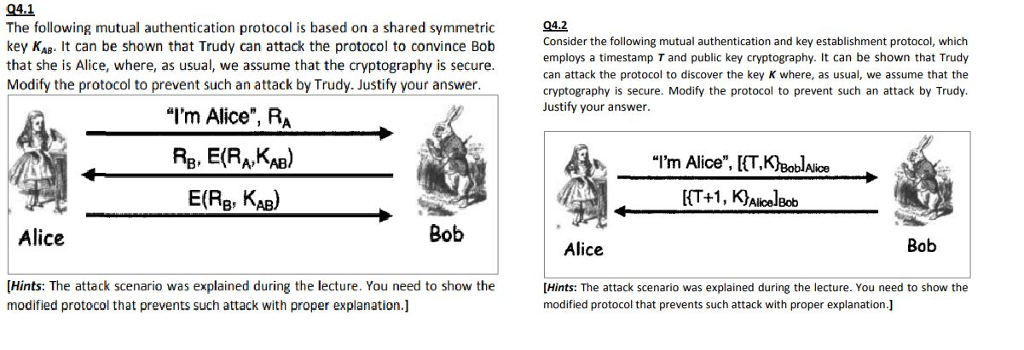
94.1 The following mutual authentication protocol is based on a shared symmetric key KAB. It can be shown that Trudy can attack the protocol to convince Bob that she is Alice, where, as usual, we assume that the cryptography is secure. Modify the protocol to prevent such an attack by Trudy. Justify your answer Q4.2 Consider the following mutual authentication and key establishment protocol, which employs a timestamp T and public key cryptography. It can be shown that Trudy can attack the protocol to discover the key K where, as usual, we assume that the cryptography is secure. Modify the protocol to prevent such an attack by Trudy. Justify your answer. "I'm Alice", RA "I'm Alice", [fT, KIBoblAlioe E(RB, KAB) AlicelBob Alice Bob Alice Bob [Hints: The attack scenario was explained during the lecture. You need to show the modified protocol that prevents such attack with proper explanation.] [Hints: The attack scenario was explained during the lecture. You need to show the modified protocol that prevents such attack with proper explanation.]
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


