Question: Read Chapter 3 ' s Closing Case Two: Direct - to - Consumer: The Warby Parker Way and respond to the four questions below (
Read Chapter s Closing Case Two: DirecttoConsumer: The Warby Parker Way and respond to the four questions below note that the chapter in text only has three questions Be sure to use the Rubric as a guide to the requirements.
Questions:
Why does DTC allow a company to offer products at a lower cost than traditional manufactures?
What is the relationship between disintermediation and a DTC business model?
What types of Clickstream analytics will a DTC business want to monitor on its website to ensure success?
Discuss a startup that has caught your attention over this past year. Briefly describe the startup and what it expects to accomplish is it in the industry? the loT industry? or
Your paper should include an introduction and responses to the four question in a paper format. Please do not bullet points for your answers and do not list the case questions. Consider using subheadings and write a paper that flows from paragraph to paragraph. Use APA format doublespaced and cite any resources
Grading Rubric:
tableRequired Elements of the Closing Case Two: Direct to Consumer,PointsTitle page with your name, course, title, and date,tableResponses that reflect your understanding of each of the four questions points for eachquestiontableWriting is coherent and supports the central idea in an APA format, with correct grammar, usage,and mechanics.Chapter : Closing Case Two: Direct to Consumer Total Points,
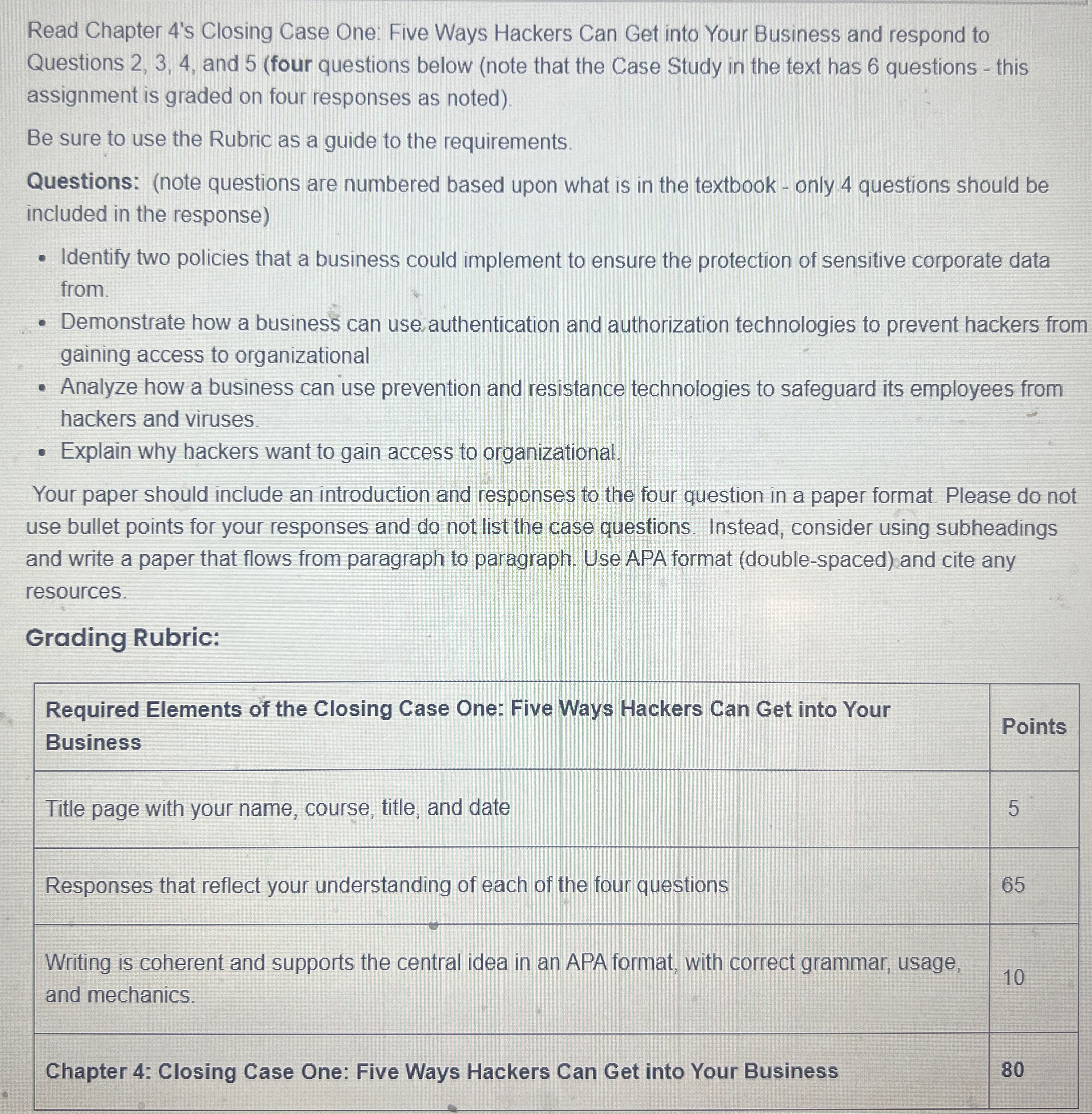
Read Chapter s Closing Case One: Five Ways Hackers Can Get into Your Business and respond to Questions and four questions below note that the Case Study in the text has questions this assignment is graded on four responses as noted
Be sure to use the Rubric as a guide to the requirements.
Questions: note questions are numbered based upon what is in the textbook only questions should be included in the response
Identify two policies that a business could implement to ensure the protection of sensitive corporate data from.
Demonstrate how a business can use authentication and authorization technologies to prevent hackers from gaining access to organizational
Analyze how a business can use prevention and resistance technologies to safeguard its employees from hackers and viruses.
Explain why hackers want to gain access to organizational.
Your paper should include an introduction and responses to the four question in a paper format. Please do not use bullet points for your responses and do not list the case questions. Instead, consider using subheadings and write a paper that flows from paragraph to paragraph. Use APA format doublespaced and cite any resources.
Grading Rubric:
tabletableRequired Elements of the Closing Case One: Five Ways Hackers Can Get into YourBusinessPointsTitle page with your name, course, title, and date,Responses that reflect your understanding of each of the four questions,tableWriting is coherent and supports the central idea in an APA format, with correct grammar, usage,and mechanics.Chapter : Closing Case One: Five Ways Hackers Can Get into Your Business,
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


