Question: Read the article below: Information Systems and Internal Control. Write: Develop a bulleted list of 1or 2 issues or best practices that you identified based
Read the article below: Information Systems and Internal Control.
Write: Develop a bulleted list of 1or 2 issues or best practices that you identified based on your reading of this article and how it may impact you while performing in an accounting position.
Information Systems and Internal Control:
IT Risk Assessment
Executive Summary Report Executive Summary
Engagement Scope and Objectives
Scope
The objective of the engagement was to perform an IT Risk Assessment for XYZ Company, through the identification and evaluation of controls using the Assessor Company Control Framework. The computer applications and related IT processes were identified for inclusion in the assessment based on criteria such as criticality, financial impact, and operational support. The applications identified for the assessment are listed in a section that follows, along with a processing flow diagram. The results solely rest on the documentation provided for review and the information obtained in the interviews with XYZ Company staff; testing was not performed as part of the Risk Assessment.
Risk Assessment
The Risk Assessment process examines the IT applications and infrastructure to identify areas that are critical to XYZ Company operations and then evaluates controls present to determine areas of risk for these processes. The risk assessment was performed through the collection and examination of XYZ Company documentation, a self-assessment survey, and interviews with key staff and management. Assessor Company's approach is detailed below.
Assessor Company Approach
In developing the IT Risk Assessment, an Assessor Company staff member performed the following tasks:
- Interviewed key personnel within the XYZ Company IT organization, to determine:
● Recent organizational changes,
● Recent technology changes, and
● Auditable universe.
- Obtained selected documentation and information from various sources, including IT and Internal Audit.
- Distributed an IT Risk Assessment survey which was completed by various IT staff within XYZ Company.
- Reviewed recent IT SOX audit reports performed by Internal Audit and by the external auditors.
Developed an audit plan based on the planning strategy:
- Determine the auditable units,
- Assign a risk rating to each audit unit based on the Risk Assessment conducted, and on subjective criteria,
- Identify the nature of the audit procedures that may be performed, and
- Identify the type and timeframe/frequency of reviews for each auditable unit. Determine if there are any mandatory annual audit requirements.
- Review the draft IS Audit Plan with Corporate IS management and Internal Audit management and adjust the nature of audit procedures and timeframe as appropriate.
During this assessment, Assessor Company did not perform any testing of any XYZ Company controls, policies, procedures, or methodologies. The controls examined relate to the core areas within IT and were assessed to identify any potential control risks within the following framework:
Control Framework
Organization" – governance, policy, organization, and compliance
Access – management and administration of user and administrative access
Network – management and administration of user and administrative access Change
Management – approvals, testing, and separation of duties
Operations – monitoring, asset management, physical and network security
XYZ Company IT Organization
Interviews were conducted as part of the information gathering phase and as a validation of the analysis of the control risks. The contents of the interviews included key applications, process flows, and organizational responsibilities. Below is an organization chart that reflects the scope of this IT risk assessment.
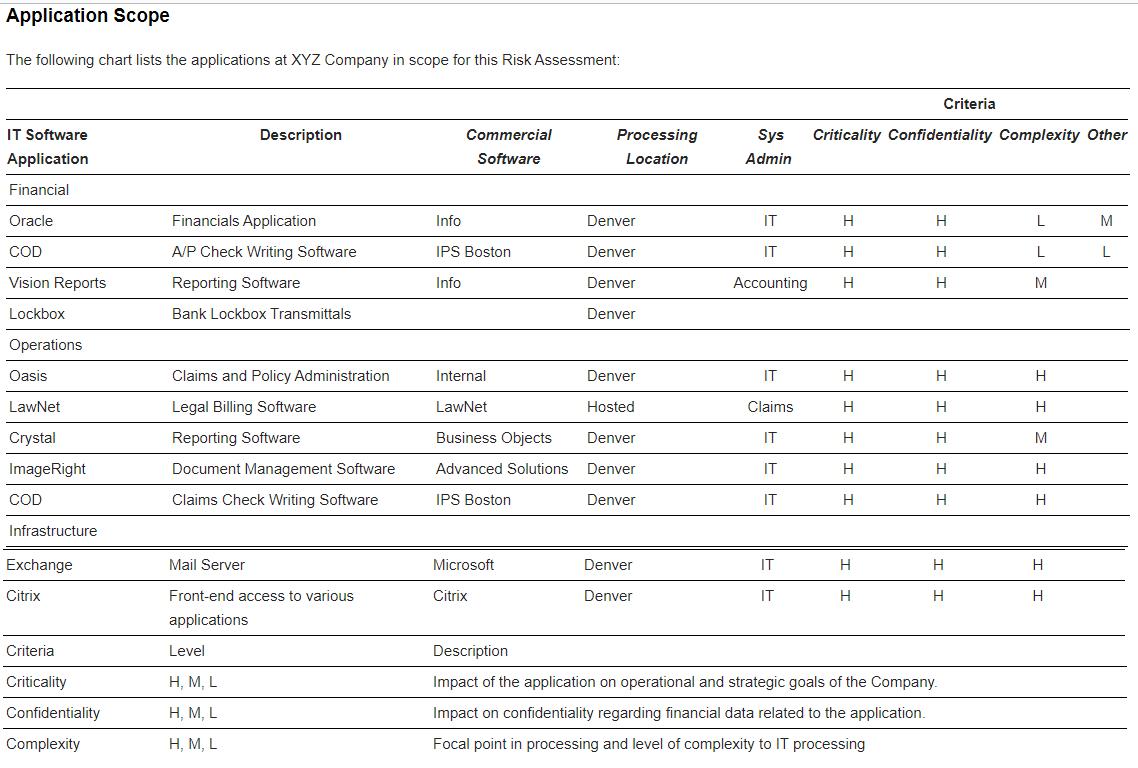
Application Scope The following chart lists the applications at XYZ Company in scope for this Risk Assessment: IT Software Application Financial Oracle COD Vision Reports Lockbox Operations Oasis LawNet Crystal Image Right COD Infrastructure Exchange Citrix Criteria Criticality Confidentiality Complexity Description Financials Application A/P Check Writing Software Reporting Software Bank Lockbox Transmittals Claims and Policy Administration Legal Billing Software. Reporting Software Document Management Software Claims Check Writing Software Mail Server Front-end access to various applications Level H, M, L H, M, L H, M, L Commercial Software Info IPS Boston Info Internal LawNet Business Objects Advanced Solutions IPS Boston Microsoft Citrix Processing Location Denver Denver Denver Denver Denver Hosted Denver Denver Denver Denver Denver Sys Admin IT IT Accounting IT Claims IT IT IT IT IT Criticality Confidentiality Complexity Other H H H H H H H H H H Criteria H H H H H H H H H H Description Impact of the application on operational and strategic goals of the Company. Impact on confidentiality regarding financial data related to the application. Focal point in processing and level of complexity to IT processing L L M H H M H H H H M L
Step by Step Solution
3.41 Rating (151 Votes )
There are 3 Steps involved in it
Write Develop a bulleted list of 1or 2 issues or best practices that you identified based on you... View full answer

Get step-by-step solutions from verified subject matter experts


