![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()



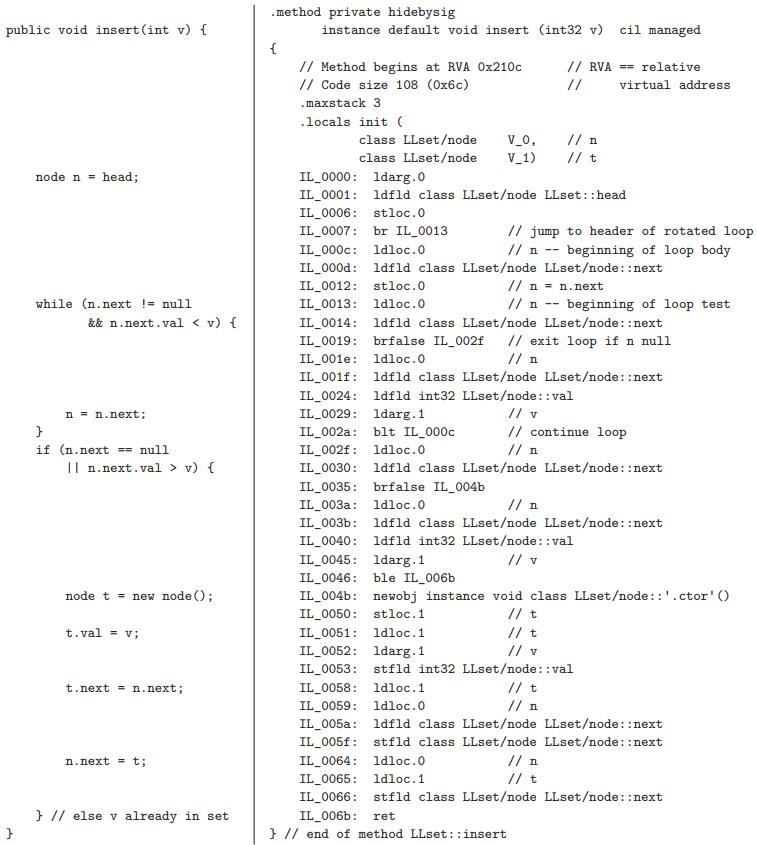
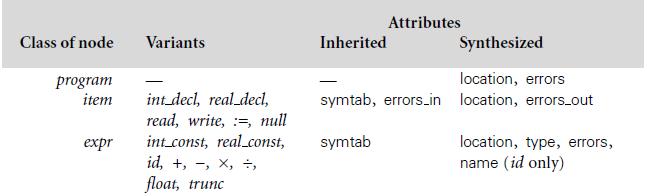
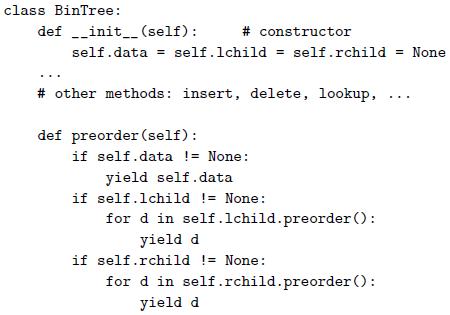
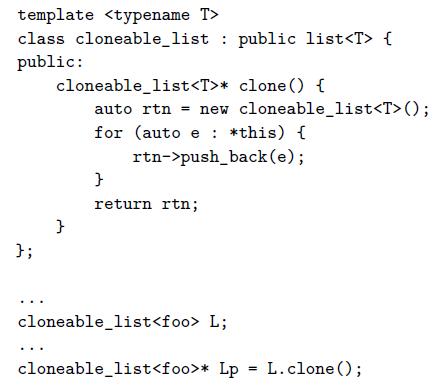
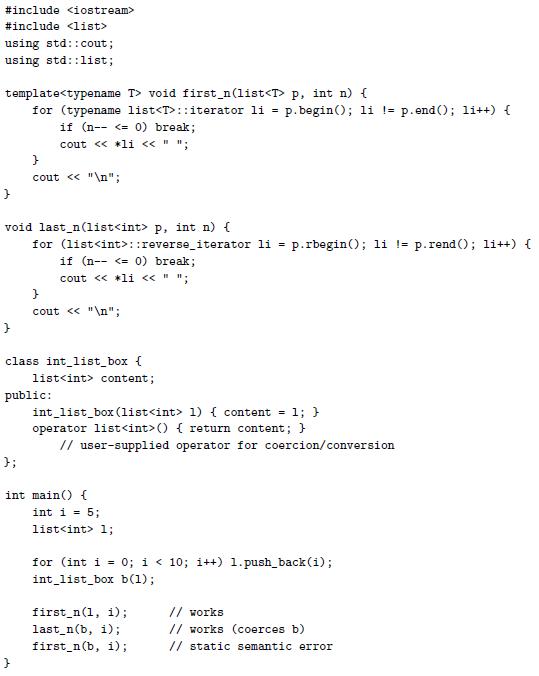
![sp- Ada: -- procedure foo(size : integer) is M : array (1..size, 1..size) of long float; Variable-size M part of the frame begin Temporaries ... end foo; Local Pointer to M variables Dope vector Fixed-size part of the frame // C99: void foo (int size) { Bookkeeping double M[size] [size];](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1606/2/1/1/3275fbcd6ff812ba1606211327427.jpg)
![sp- Ada: -- procedure foo (size : integer) is M : array (1..size, 1..size) of long float; Variable-size M part of the frame begin Temporaries ... end foo; Local Pointer to M variables Dope vector Fixed-size part of the frame // C99: void foo (int size) { Bookkeeping double M[size]](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1606/2/1/1/4125fbcd754e073b1606211412089.jpg)
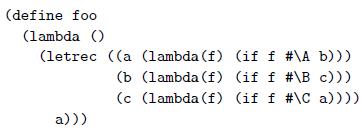

![class string_map { string cached_key; string cached_val; const string complex_lookup(const string key); // body specified elsewhere public: const string operator [] (const string key) { if (key == cached_key) return cached_val; string rtn_val = complex_lookup (key); cached_key key; cached_val = rtn_val; return rtn_val; };](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1606/2/1/5/3285fbce6a0e8af21606215329072.jpg)
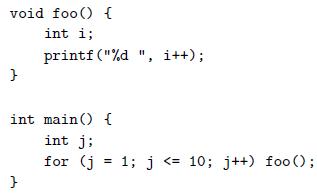
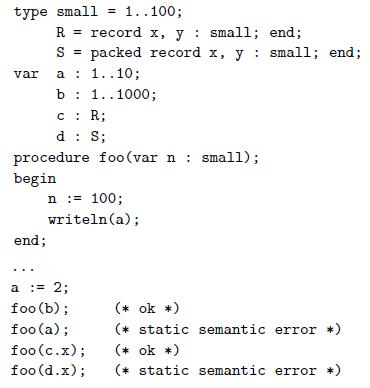

![#include #include #include char* days [7] {](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1606/2/1/5/0375fbce57d823a51606215037724.jpg)
![#include #include #include char* days [7] = {](https://dsd5zvtm8ll6.cloudfront.net/si.question.images/images/question_images/1606/2/1/6/1165fbce9b41f4de1606216116293.jpg)