Question: Consider the following mutual authentication and key establishment protocol, which employs a timestamp T and public key cryptography. Show that Trudy can attack the protocol
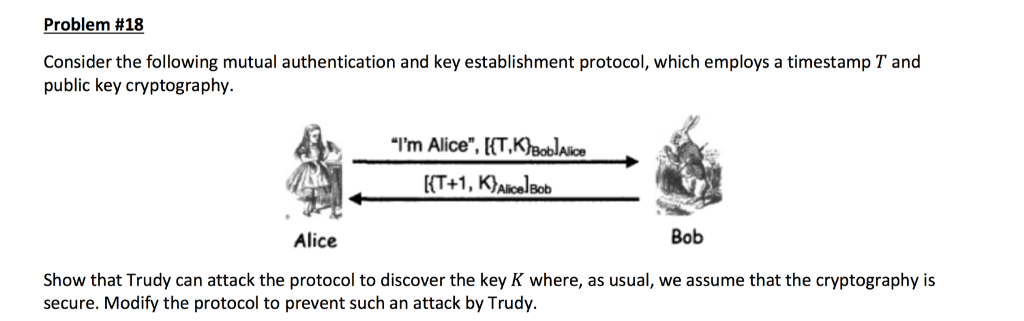
Consider the following mutual authentication and key establishment protocol, which employs a timestamp T and public key cryptography. Show that Trudy can attack the protocol to discover the key K where, as usual, we assume that the cryptography is secure. Modify the protocol to prevent such an attack by Trudy
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


