![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()







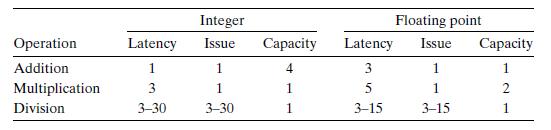
![1 2 3 4 5 6 7 8 9 10 11 double poly (double a[], double x, long degree) { } long i; double result = a [0];](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/1/8/5746538c24e524341698218573252.jpg)

![[00101] [00011] [10111] [00010] [01100] y [10001] [11000] [00010] [10100] [00100] x + x x + y | || Case |||](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/6/84165375bf9e8071Untitled.png)
![x y -8 -5 [1000] [1011] -8 [1000] -8 [1000] 2 [0010] 5 [0101] -8 [1000] 5 [0101] 5 [0101] 5 [0101] x+y -13](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/6/86065375c0c5f32c1698126858725.jpg)
![1 2 3 4 5 6 7 8 9 /* WARNING: This is buggy code */ float sum_elements (float a[], unsigned length) { } int](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/6/333653759fd9dd4c1698126332018.jpg)


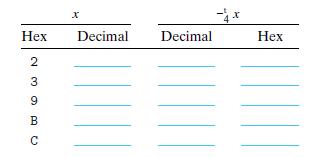
![x Hexadecimal Binary OXA [1010] 0x1 OxB 0x2 0x7 0xC B2U4(x) 2 +2=10 B2T4(x) -2 +2=-6](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/5/2146537559e250f61698125212603.jpg)
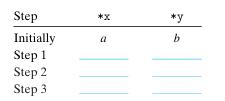
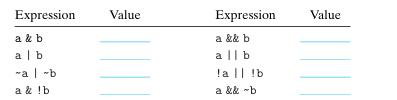
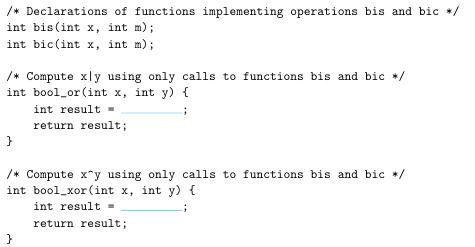

![Operation b "a -b a&b alb a b Result [01001110] [11100001]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/1/2/1/959653748e785f261698121956776.jpg)





![1234567 8 9 10 11 12 13 int productarray3d (int a[N] [N] [N]) int i, j, k, product for (i = N-1; i >= 0; i--)](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/2/0986538d012bca7a1698222097652.jpg)
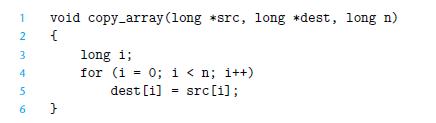
![1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 void merge (long src1[], long src2[], long dest [], long n) { long 11 =](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/0/0106538c7ea20ccf1698220009046.jpg)
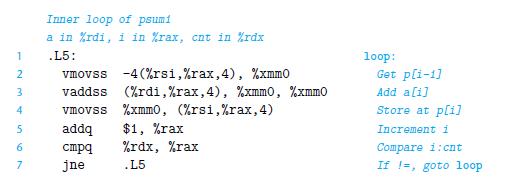
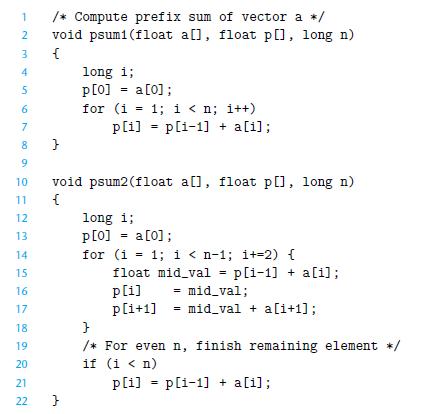
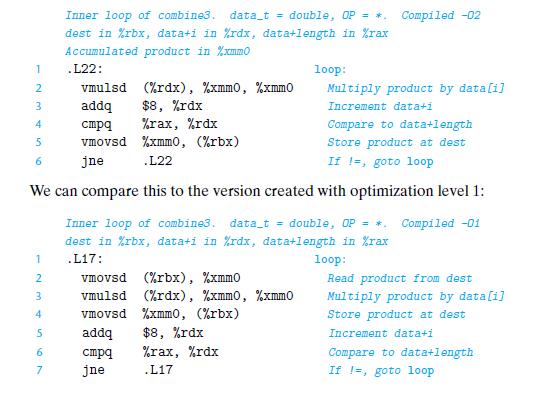
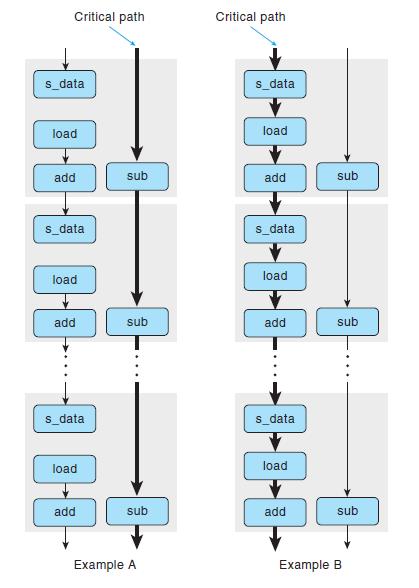
![%xmmo mul %xmmo load %rax %rdx cmp jne (a) add %rdx data [/] %xmmo load mul %xmmo (b) %rdx add %rdx](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/0/2696538c8ed04f871698220267917.jpg)
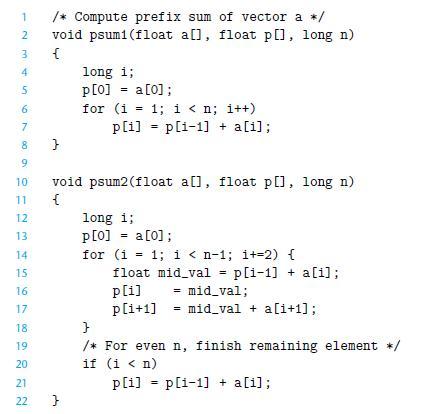

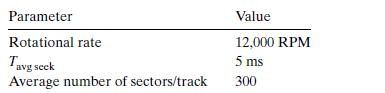
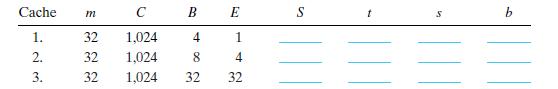
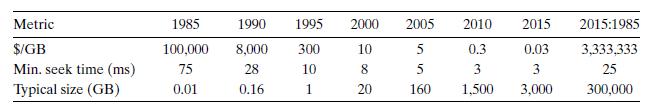
![int array [4096]; for (i = 0; i < 4096; i++) sum += array[i];](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/2/4096538d14964b5f1698222408295.jpg)
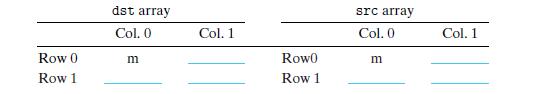
![1 2 3 4 5 6 7 8 9 typedef int array [2] [2]; void transpose1 (array dst, array src) { 10 11 12 } int i, j;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/3/4416538d551433ef1698223440136.jpg)
![1 2 3 4 5 6 7 8 struct algae_position { int x; int y; }; struct algae_position grid [32] [32]; int total_x =](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/3/5826538d5dec94d11698223576454.jpg)
![1 2 WN 3 4 5 6 789 10 11 for (i = 31; i >= 0; i--) { } for (j = 31; j >= 0; j--) { total_x += grid [i][j].x;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/3/6326538d610910cf1698223631235.jpg)
![1 2 3 4 5 6 for (i = 31; i >= 0; i--) { } for(j= 31; j = 0; j--) { total_x += grid [j] [i].x; total_y += grid](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/7/2366538e4242e33e1698227234376.jpg)
![1 23 2 3 4 5 6 for (i = 31; i >= 0; i--) { for (j = 31; j total_x + total y + } } = 0; j--) { grid [i][j].x;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/2/7/3526538e4986f5051698227350622.jpg)
![1 2 3 4 5 6 7 8 9 void swap(); int buf [2] = {1, 2}; int main() } swap(); return 0;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/3/6/98665390a3a1cd051698236983730.jpg)
![1 2 3 4 5 6 7 8 9 extern int buf []; int *bufpo=&buf [0]; int *bufp1; void swap() { 10 11 12 13 14 } int](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/3/6/99865390a4695e221698236996627.jpg)
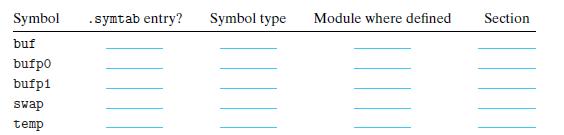
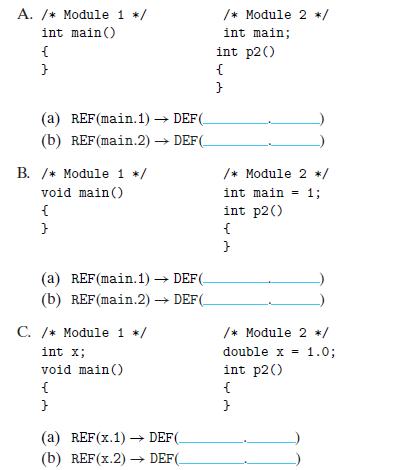
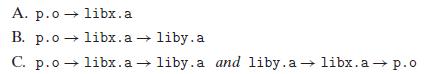
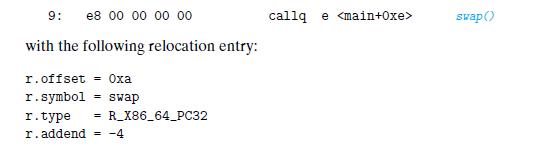
![(a) m.c 1 void swap(); 2 3 int buf [2] = {1, 2}; 45 5 int main() 6 { 7 8 9} swap(); return 0;](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/3/7/18565390b0135c9c1698237182582.jpg)
![(b) swap.c 1 2 3 4 5 6 7 8 9 10 11 12 13 14 extern int buf []; int *bufp0 = &buf [0]; int *bufp1; void swap()](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/3/7/21365390b1d1a7a11698237211119.jpg)
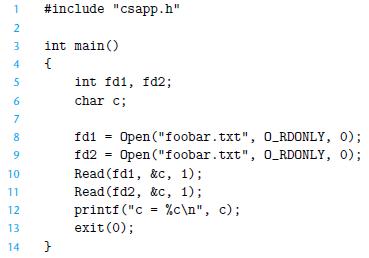
![linux> ./myecho argi arg2 Command-ine arguments: argv[0]: myecho argv[ 1]: argi argv[ 2] arg2 Environment](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/2/3/1/9506538f68e3829bUntitled.png)