Question: For the following mutual authentication protocol, where k is a shared secret key between Alice and Bob, show how an attacker Trudy can use reflection
For the following mutual authentication protocol, where k is a shared secret key between Alice and Bob, show how an attacker Trudy can use reflection attack to impersonate Bob. 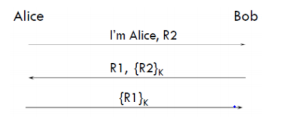
Bob Alice I'm Alice, R2 R1, (R2) (R1)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


