![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()


![Register indirect + increment: LD Rj Ri ST Rj Ri Decrement + register indirect: LD Rj Ri ST Rj Ri Rj+M[Ri]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/5/7/0/9336599b0353eae91704570929561.jpg)
![IN R[DR] ADRS OUT ADRS R[SB]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/5/7/0/9696599b0592cda91704570967383.jpg)
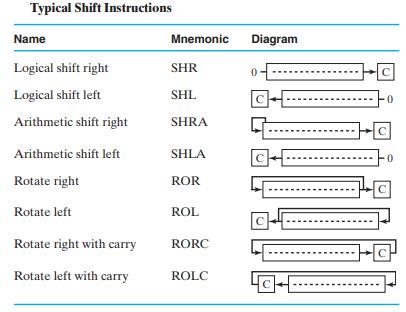
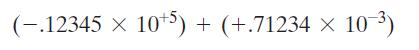
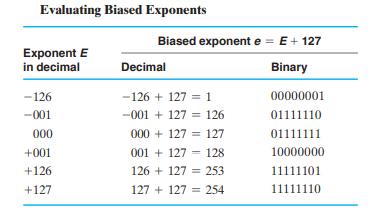

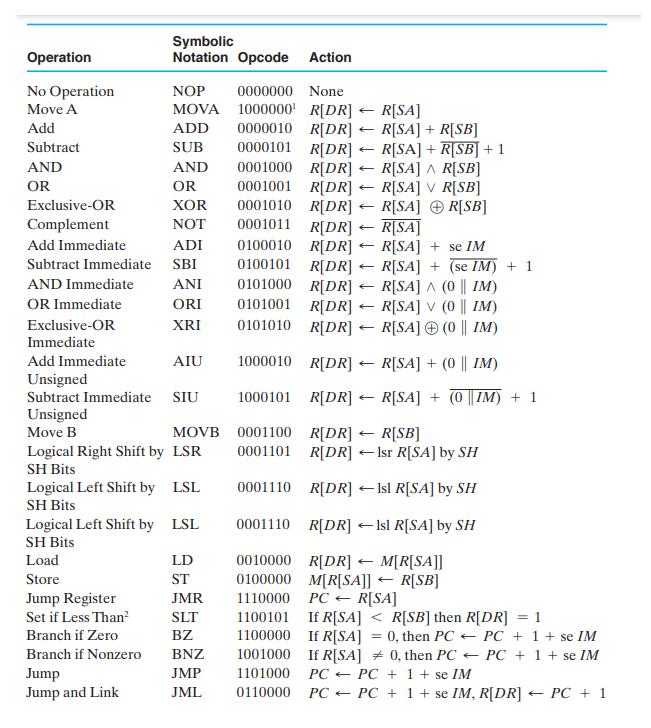
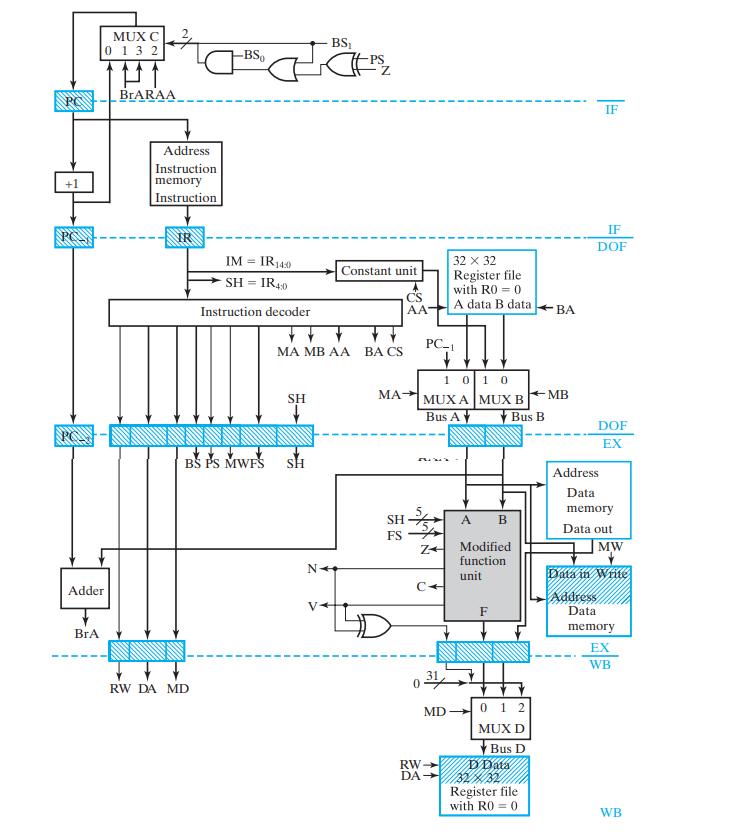
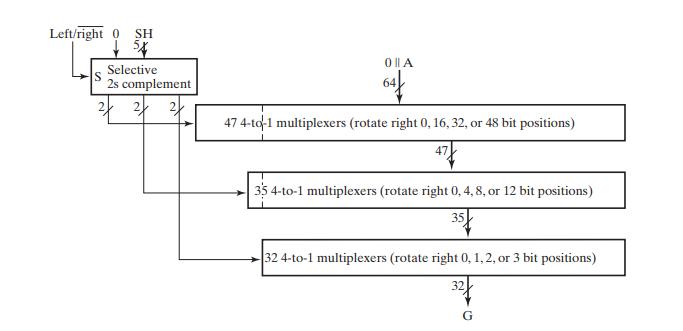
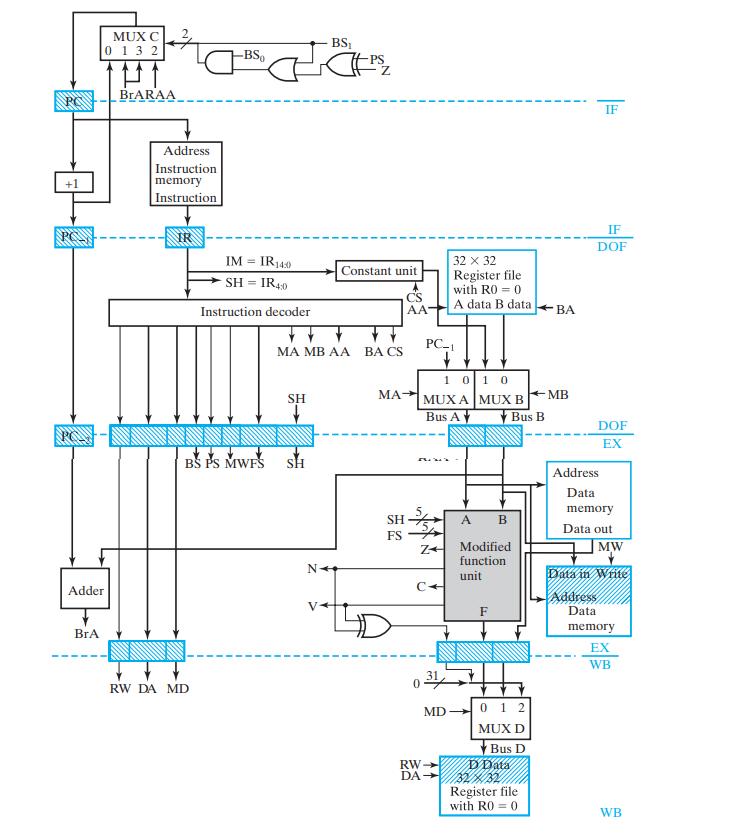
![Control Words for Instructions Symbolic Notation Action NOP None MOVA R[DR] 1 R[SA] ADD R[DR] SUB AND OR XOR](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/5/7/3/5126599ba48092f31704573508297.jpg)

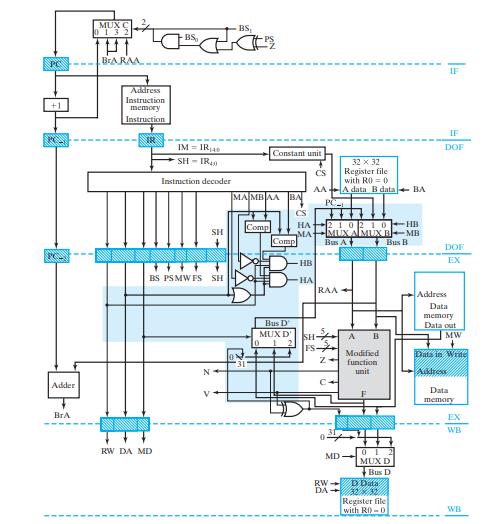

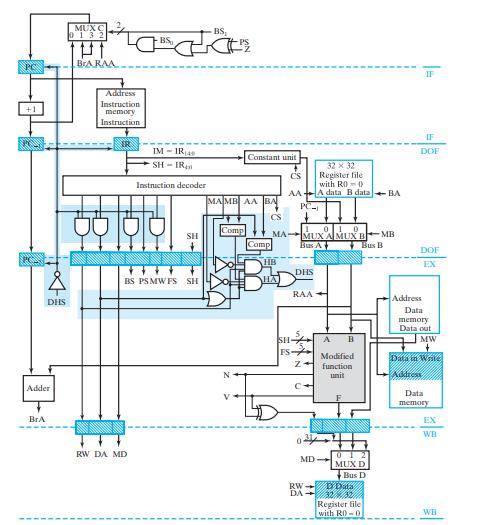
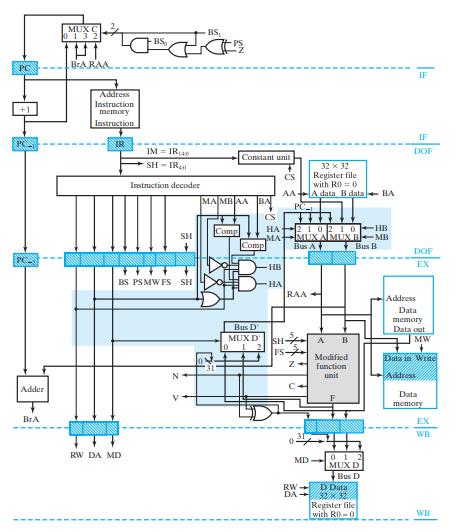
![(a) Push: R[SA] DR=SA. R[SA] + 1 followed by M[R[SA]] R[SB]. Assume (b) Pop: R[DR] M[R[SA]] followed by](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/5/7/4/5426599be4e5df141704574540551.jpg)
![(a) Add Memory Indirect: R[DR] (b) Add to Memory: M[R[DR]] M[R[SA]] + R[SB] R[SA] + M[M[R[SB]]]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/5/7/4/6346599beaac3b041704574632958.jpg)
![(a) Add with carry: R[DR] R[SA] + R[SB] + C (b) Subtract with borrow: R[DR] R[SA] R[SB] - B -](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1704/5/7/4/6116599be93340691704574609329.jpg)