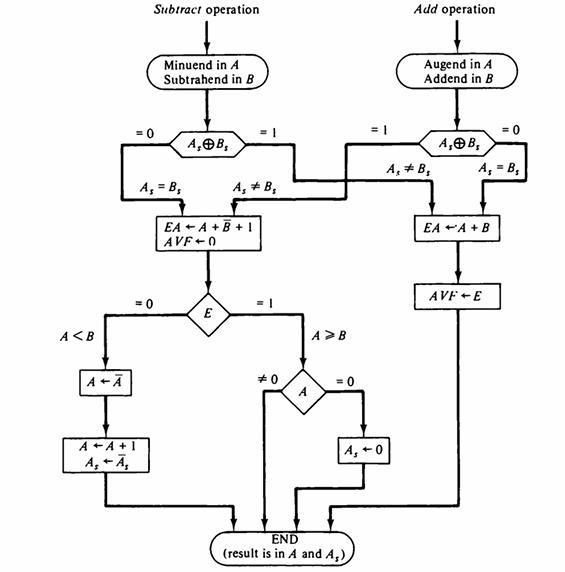
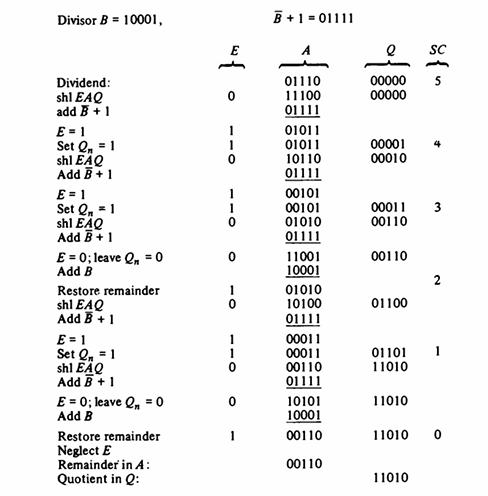
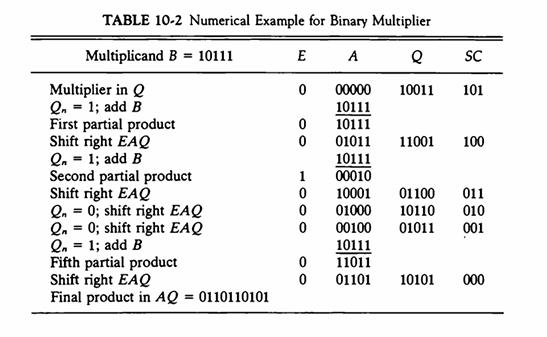
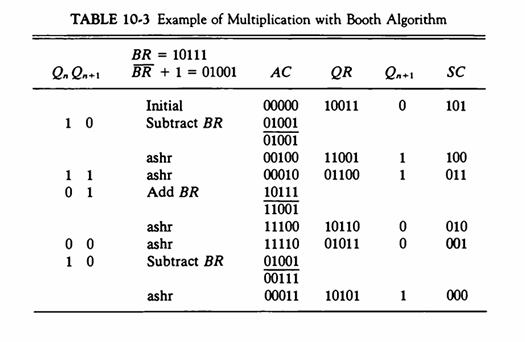
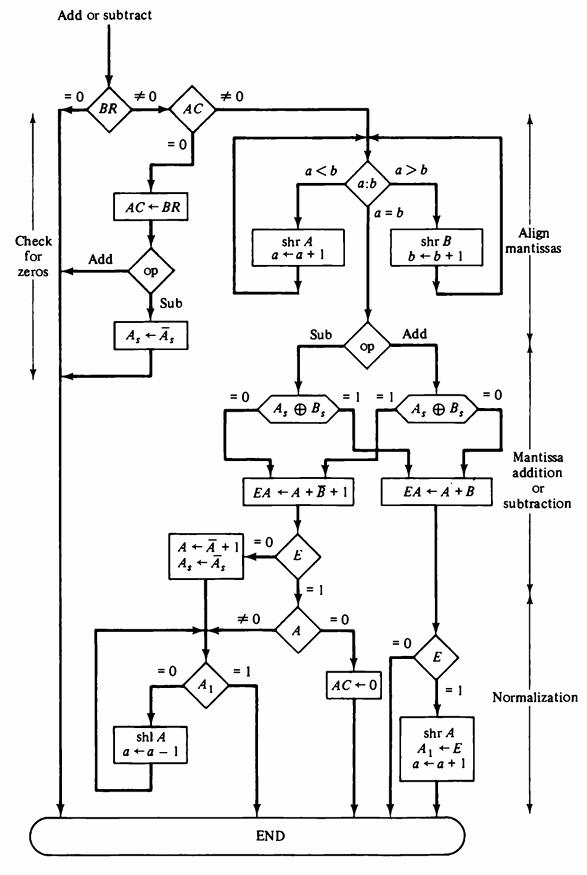
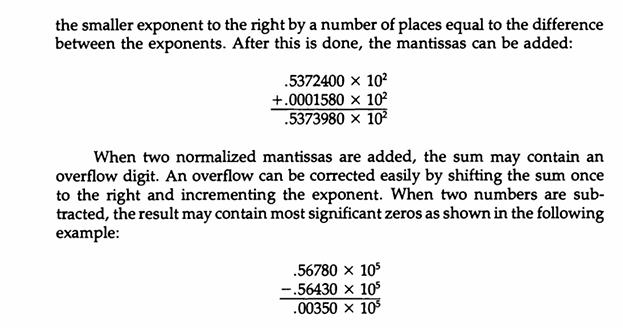
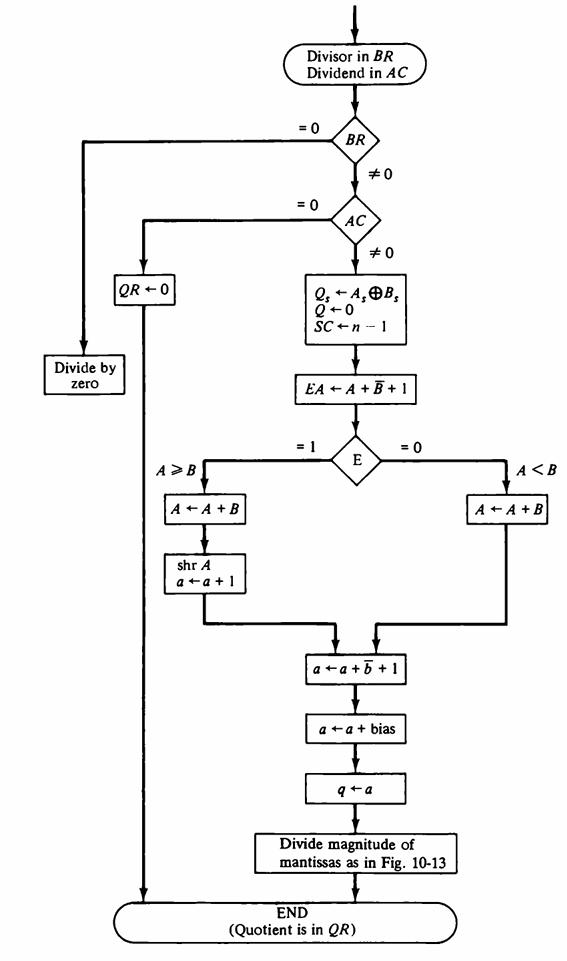
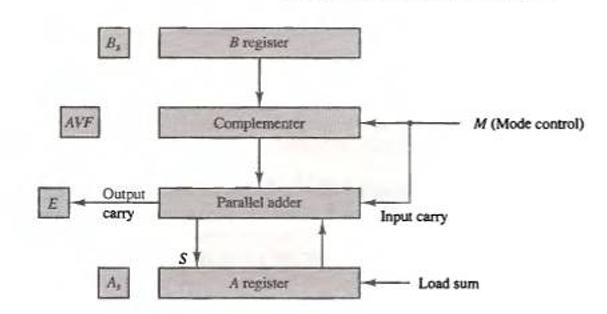
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()



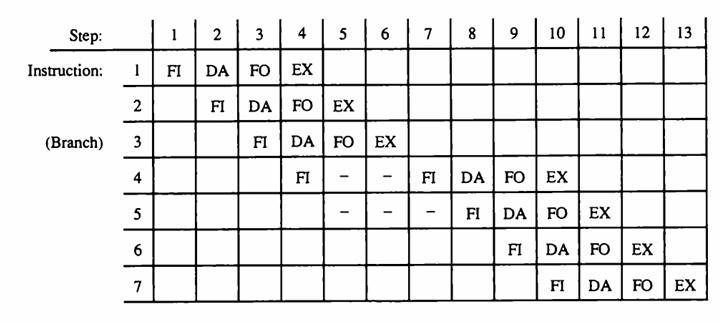
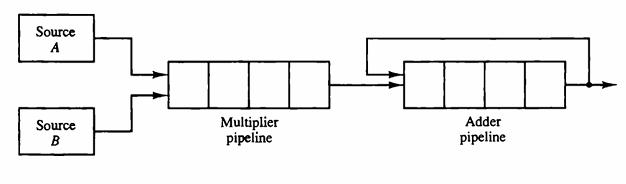
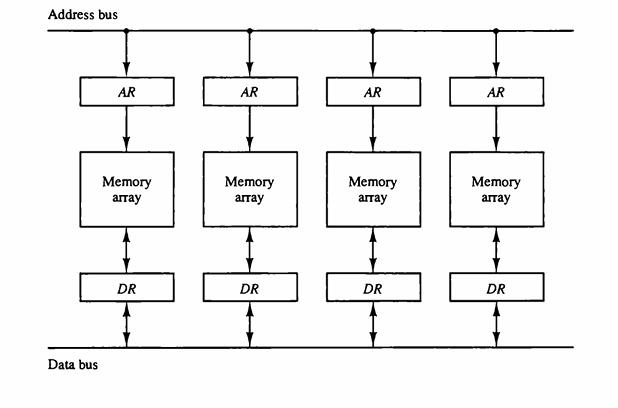
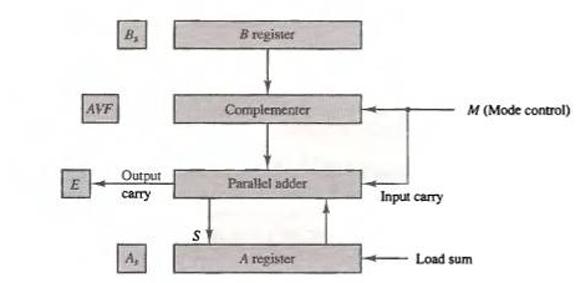
![Delayed Load Consider now the operation of the following four instructions: 1. LOAD: R1-M[address 1]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/0/6/5/61565366ccfdb6aeimage_%282%29.png)
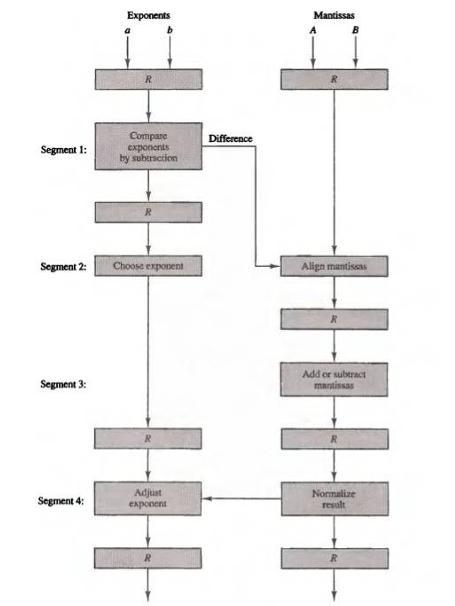

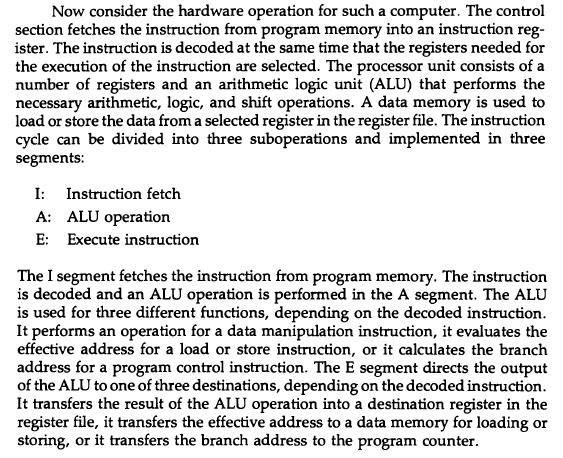
![Delayed Load Consider now the operation of the following four instructions: 1. LOAD: R1-M[address 1]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/0/6/5/69165366d1b2fb47image_%282%29.png)

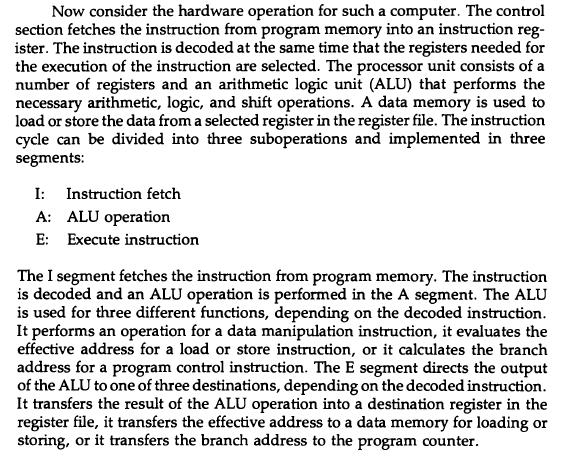
![Delayed Load Consider now the operation of the following four instructions: 1. LOAD: R1M[address 1]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/0/6/5/74665366d529e0eaimage_%282%29.png)

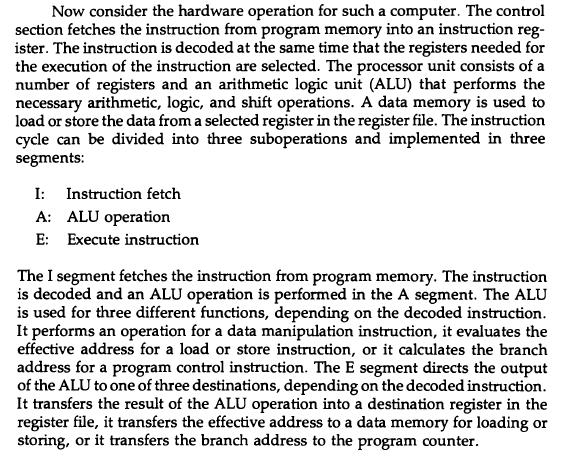
![Delayed Load Consider now the operation of the following four instructions: 1. LOAD: R1M[address 1]](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/0/6/5/80565366d8d74a68image_%282%29.png)
![Load ADD INC STORE R1-M[312] R2 R2 + M[313] R3 R3 +1 M[314] R3](https://dsd5zvtm8ll6.cloudfront.net/images/question_images/1698/0/4/7/75265362708a47eb1698047749364.jpg)